Hello everyone,
I hope you can help me
I am trying to set up a VPN tunnel between two Vyos version 1.3.6 routers on a virtual platform where they are connected to a virtual router.
The scenario is the following:
Each vyos router has a single interface with the internal IP and a floating IP with which it goes out to the Internet. The floating one is assigned to the same internal network port so I don’t have 2 separate interfaces but all in one.
The device has access to the Internet and there is nothing filtered by security rules between the two deployed vyos, you can ping between them without problem
The config is the following:
R1
set vpn ipsec esp-group bcn-esp compression ‘disable’
set vpn ipsec esp-group bcn-esp lifetime ‘1800’
set vpn ipsec esp-group bcn-esp mode ‘tunnel’
set vpn ipsec esp-group bcn-esp pfs ‘disable’
set vpn ipsec esp-group bcn-esp proposal 1 encryption ‘aes256’
set vpn ipsec esp-group bcn-esp proposal 1 hash ‘sha1’
set vpn ipsec ike-group bcn-ike ikev2-reauth ‘no’
set vpn ipsec ike-group bcn-ike key-exchange ‘ikev1’
set vpn ipsec ike-group bcn-ike lifetime ‘1800’
set vpn ipsec ike-group bcn-ike proposal 1 encryption ‘aes256’
set vpn ipsec ike-group bcn-ike proposal 1 hash ‘sha1’
set vpn ipsec ipsec-interfaces interface ‘eth0’
set vpn ipsec site-to-site peer PUBLIC IP R2 authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer PUBLIC IP R2 authentication pre-shared-secret ‘Password’
set vpn ipsec site-to-site peer PUBLIC IP R2 ike-group ‘bcn-ike’
set vpn ipsec site-to-site peer PUBLIC IP R2 local-address ‘IP PUBLIC R1’
set vpn ipsec site-to-site peer PUBLIC IP R2 tunnel 0 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer PUBLIC IP R2 tunnel 0 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer PUBLIC IP R2 tunnel 0 esp-group ‘bcn-esp’
set vpn ipsec site-to-site peer PUBLIC IP R2 tunnel 0 local prefix ‘192.168.1.0/24’
set vpn ipsec site-to-site peer PUBLIC IP R2 tunnel 0 remote prefix ‘172.16.2.0/24’
R2
set vpn ipsec esp-group mad-esp compression ‘disable’
set vpn ipsec esp-group mad-esp lifetime ‘1800’
set vpn ipsec esp-group mad-esp mode ‘tunnel’
set vpn ipsec esp-group mad-esp pfs ‘disable’
set vpn ipsec esp-group mad-esp proposal 1 encryption ‘aes256’
set vpn ipsec esp-group mad-esp proposal 1 hash ‘sha1’
set vpn ipsec ike-group mad-ike ikev2-reauth ‘no’
set vpn ipsec ike-group mad-ike key-exchange ‘ikev1’
set vpn ipsec ike-group mad-ike lifetime ‘1800’
set vpn ipsec ike-group madike proposal 1 encryption ‘aes256’
set vpn ipsec ike-group mad-ike proposal 1 hash ‘sha1’
set vpn ipsec ipsec-interfaces interface ‘eth0’
set vpn ipsec site-to-site peer PUBLIC IP R1 authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer PUBLIC IP R1 authentication pre-shared-secret ‘not-so-secret’
set vpn ipsec site-to-site peer PUBLIC IP R1 ike-group ‘mad-ike’
set vpn ipsec site-to-site peer PUBLIC IP R1 local-address ‘IP PUBLIC R2’
set vpn ipsec site-to-site peer PUBLIC IP R1 tunnel 0 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer PUBLIC IP R1 tunnel 0 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer PUBLIC IP R1 tunnel 0 esp-group ‘mad-esp’
set vpn ipsec site-to-site peer PUBLIC IP R1 tunnel 0 local prefix ‘172.16.2.0/24’
set vpn ipsec site-to-site peer PUBLIC IP R1 tunnel 0 remote prefix ‘192.168.1.0/24’
On the virtual routers I have SNAT enabled
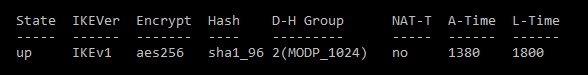
that’s why I haven’t configured any nat in vyos. I always have the tunnel on down

I enable nat traversal in esp group and it doesn’t work either