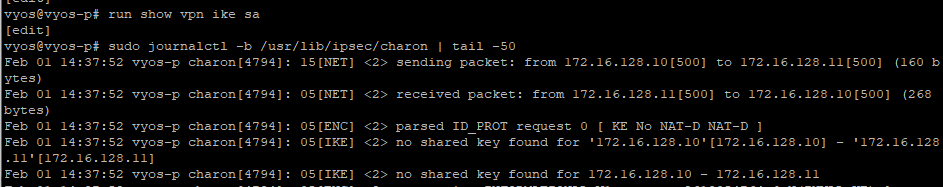
the command show vpn ipsec sa and ike sa show nothing both ike and ipsec is failing
vyos-p charon[4794]: 05[IKE] <2> no shared key found for ‘172.16.128.10’[172.16.128.10] - ‘172.16.128.11’[172.16.128.11]
i don’t know what am i missing
router1 config
set vpn ipsec esp-group esp_aes256_sha256 lifetime ‘3600’
set vpn ipsec esp-group esp_aes256_sha256 mode ‘tunnel’
set vpn ipsec esp-group esp_aes256_sha256 pfs ‘dh-group2’
set vpn ipsec esp-group esp_aes256_sha256 proposal 1 encryption ‘aes256’
set vpn ipsec esp-group esp_aes256_sha256 proposal 1 hash ‘sha256’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection action ‘clear’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection interval ‘30’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection timeout ‘90’
set vpn ipsec ike-group ike_aes256_sha256 key-exchange ‘ikev1’
set vpn ipsec ike-group ike_aes256_sha256 lifetime ‘28800’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 dh-group ‘2’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 encryption ‘aes256’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth9’
set vpn ipsec site-to-site peer vyos2-ipsec authentication local-id ‘172.16.128.10’
set vpn ipsec site-to-site peer vyos2-ipsec authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer vyos2-ipsec authentication remote-id ‘172.16.128.11’
set vpn ipsec site-to-site peer vyos2-ipsec connection-type ‘initiate’
set vpn ipsec site-to-site peer vyos2-ipsec default-esp-group ‘esp_aes256_sha256’
set vpn ipsec site-to-site peer vyos2-ipsec ike-group ‘ike_aes256_sha256’
set vpn ipsec site-to-site peer vyos2-ipsec local-address ‘172.16.128.10’
set vpn ipsec site-to-site peer vyos2-ipsec remote-address ‘172.16.128.11’
set vpn ipsec authentication psk key id ‘172.16.128.10’
set vpn ipsec authentication psk key secret ‘xxx’
set vpn ipsec site-to-site peer vyos2-ipsec tunnel 0 esp-group ‘esp_aes256_sha256’
set vpn ipsec site-to-site peer vyos2-ipsec tunnel 0 local prefix ‘192.168.2.0/24’
set vpn ipsec site-to-site peer vyos2-ipsec tunnel 0 remote prefix ‘192.168.3.0/24’
router 2:
set vpn ipsec esp-group esp_aes256_sha256 lifetime ‘3600’
set vpn ipsec esp-group esp_aes256_sha256 mode ‘tunnel’
set vpn ipsec esp-group esp_aes256_sha256 pfs ‘dh-group2’
set vpn ipsec esp-group esp_aes256_sha256 proposal 1 encryption ‘aes256’
set vpn ipsec esp-group esp_aes256_sha256 proposal 1 hash ‘sha256’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection action ‘clear’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection interval ‘30’
set vpn ipsec ike-group ike_aes256_sha256 dead-peer-detection timeout ‘90’
set vpn ipsec ike-group ike_aes256_sha256 key-exchange ‘ikev1’
set vpn ipsec ike-group ike_aes256_sha256 lifetime ‘28800’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 dh-group ‘2’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 encryption ‘aes256’
set vpn ipsec ike-group ike_aes256_sha256 proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth10’
set vpn ipsec site-to-site peer vyos1-ipsec authentication local-id ‘172.16.128.11’
set vpn ipsec site-to-site peer vyos1-ipsec authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer vyos1-ipsec authentication remote-id ‘172.16.128.10’
set vpn ipsec site-to-site peer vyos1-ipsec connection-type ‘initiate’
set vpn ipsec site-to-site peer vyos1-ipsec default-esp-group ‘esp_aes256_sha256’
set vpn ipsec site-to-site peer vyos1-ipsec ike-group ‘ike_aes256_sha256’
set vpn ipsec site-to-site peer vyos1-ipsec local-address ‘172.16.128.11’
set vpn ipsec site-to-site peer vyos1-ipsec remote-address ‘172.16.128.10’
set vpn ipsec authentication psk key id ‘172.16.128.11’
set vpn ipsec authentication psk key secret ‘xxx’
set vpn ipsec site-to-site peer vyos1-ipsec tunnel 0 esp-group ‘esp_aes256_sha256’
set vpn ipsec site-to-site peer vyos1-ipsec tunnel 0 local prefix ‘192.168.3.0/24’
set vpn ipsec site-to-site peer vyos1-ipsec tunnel 0 remote prefix ‘192.168.2.0/24’