Hello All,
I am new to VYOS.
Trying to set up site to site tunnels between multiple locations (mesh) and also L2TP VPN server on all the vyos routers for the remote users to dial into the network.
Site-to-site works fine but not the VPN for the remote users.
If I take out the site to site config then VPN works. Users can dial-in. I am not able to make both site-to-site tunnels and l2tp/ipsec vpn work at the same time.
Any help is appreciated.
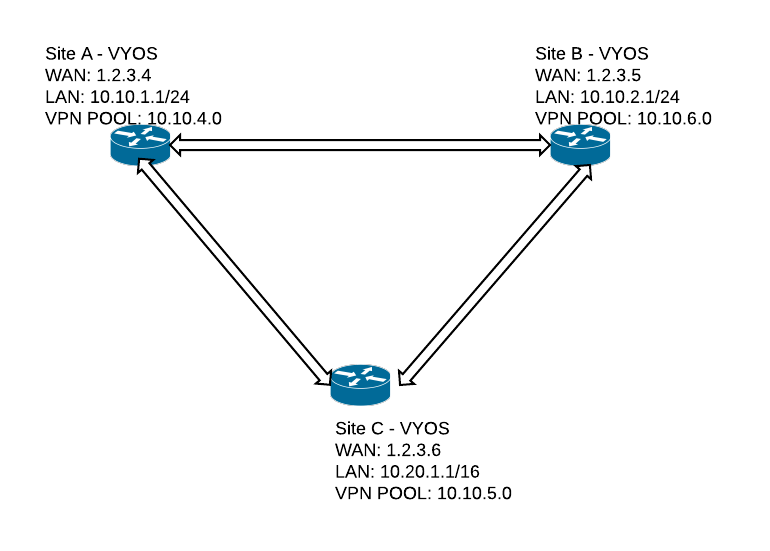
Following is my network diagram and the configuration (Site A )
interfaces {
ethernet eth0 {
address 1.2.3.4/24
duplex auto
smp_affinity auto
speed auto
}
ethernet eth1 {
address 10.10.1.1/24
duplex auto
smp_affinity auto
speed auto
}
ethernet eth2 {
duplex auto
smp_affinity auto
speed auto
}
ethernet eth3 {
duplex auto
smp_affinity auto
speed auto
}
loopback lo {
}
vti vti0 {
address 172.16.10.1/30
description "VTI between Site A and Site B"
}
vti vti1 {
address 172.16.20.1/30
description "VTI between Site A and Site C"
}
}
nat {
source {
rule 100 {
outbound-interface eth0
translation {
address masquerade
}
}
}
}
protocols {
static {
interface-route 10.10.2.0/24 {
next-hop-interface vti0 {
}
}
interface-route 10.10.5.0/24 {
next-hop-interface vti1 {
}
}
interface-route 10.10.6.0/24 {
next-hop-interface vti0 {
}
}
interface-route 10.20.0.0/16 {
next-hop-interface vti1 {
}
}
}
}
service {
dhcp-server {
disabled false
shared-network-name Site-A-pool {
authoritative enable
subnet 10.10.1.0/24 {
default-router 10.10.1.1
dns-server 10.10.1.1
lease 86400
start 10.10.1.100 {
stop 10.10.1.199
}
}
}
}
dns {
forwarding {
cache-size 150
listen-on eth1
name-server 8.8.8.8
name-server 8.8.4.4
}
}
ssh {
port 22
}
}
system {
config-management {
commit-revisions 20
}
console {
device ttyS0 {
speed 9600
}
}
gateway-address 1.2.3.1
host-name vyos-site-a
login {
user vyos {
authentication {
encrypted-password XXXXXXXX
}
level admin
}
}
ntp {
server 0.pool.ntp.org {
}
server 1.pool.ntp.org {
}
server 2.pool.ntp.org {
}
}
package {
auto-sync 1
repository community {
components main
distribution helium
password ""
url http://packages.vyos.net/vyos
username ""
}
}
syslog {
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
time-zone UTC
}
vpn {
ipsec {
esp-group ESP-Default {
compression disable
lifetime 3600
mode tunnel
pfs dh-group16
proposal 1 {
encryption aes256
hash sha256
}
}
ike-group IKE-Default {
dead-peer-detection {
action clear
interval 30
timeout 90
}
ikev2-reauth no
key-exchange ikev1
lifetime 86400
proposal 1 {
dh-group 16
encryption aes256
hash sha256
}
}
ipsec-interfaces {
interface eth0
}
logging {
log-modes all
}
nat-networks {
allowed-network 0.0.0.0/0 {
}
}
nat-traversal enable
site-to-site {
peer 1.2.3.5 {
authentication {
id 1.2.3.4
mode pre-shared-secret
pre-shared-secret XXXXXX
}
connection-type initiate
default-esp-group ESP-Default
ike-group IKE-Default
ikev2-reauth inherit
local-address 1.2.3.4
vti {
bind vti0
esp-group ESP-Default
}
}
peer 1.2.3.6 {
authentication {
id 1.2.3.4
mode pre-shared-secret
pre-shared-secret XXXXXXX
}
connection-type initiate
default-esp-group ESP-Default
ike-group IKE-Default
ikev2-reauth inherit
local-address 1.2.3.4
vti {
bind vti1
esp-group ESP-Default
}
}
}
}
l2tp {
remote-access {
authentication {
local-users {
username test {
password xxxxx
}
}
mode local
}
client-ip-pool {
start 10.10.4.1
stop 10.10.4.255
}
dns-servers {
server-1 8.8.8.8
server-2 8.8.4.4
}
ipsec-settings {
authentication {
mode pre-shared-secret
pre-shared-secret XXXXXXX
}
ike-lifetime 3600
}
outside-address 1.2.3.4
}
}
}
/* Warning: Do not remove the following line. */
/* === vyatta-config-version: "cluster@1:config-management@1:conntrack-sync@1:conntrack@1:cron@1:dhcp-relay@1:dhcp-server@4:firewall@5:ipsec@4:nat@4:qos@1:quagga@2:system@6:vrrp@1:wanloadbalance@3:webgui@1:webproxy@1:zone-policy@1" === */
/* Release version: VyOS 1.1.8 */
Thanks