Hi Everyone,
I am useing VyOS 1.3 rc6; This is the link of reference manual: L2TP — VyOS 1.3.x (equuleus) documentation
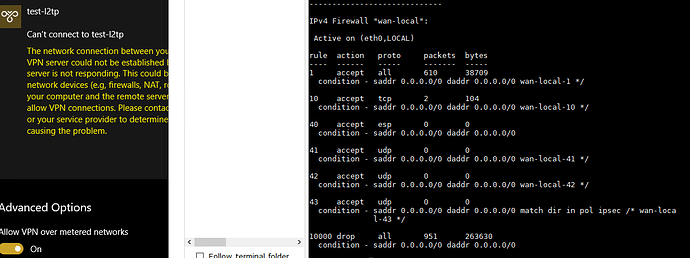
I config a L2TP over IPSec in VyOS works fine, but when I set up the firewall, VPN can not work;
I just observe that all traffic of the vpn is dropped:
What could be the reason for this state ?
Below is my configuration:
vyos@vyos# show interfaces ethernet eth0
address dhcp
firewall {
in {
name wan
}
local {
name wan-local
}
}
hw-id 00:0c:29:2b:3a:d0
vyos@vyos# show firewall name
name wan {
default-action drop
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
state {
invalid enable
}
}
}
name wan-local {
default-action drop
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 10 {
action accept
destination {
port 22
}
protocol tcp
}
rule 40 {
action accept
protocol esp
}
rule 41 {
action accept
destination {
port 500
}
protocol udp
}
rule 42 {
action accept
destination {
port 4500
}
protocol udp
}
rule 43 {
action accept
destination {
port 1701
}
ipsec {
match-ipsec
}
protocol udp
}
}
vyos@vyos# show vpn
ipsec {
ipsec-interfaces {
interface eth0
}
nat-networks {
allowed-network 0.0.0.0/0 {
}
}
nat-traversal enable
}
l2tp {
remote-access {
authentication {
local-users {
username user {
password user
}
}
mode local
}
client-ip-pool {
start 192.168.33.100
stop 192.168.33.200
}
gateway-address 192.168.33.1
ipsec-settings {
authentication {
mode pre-shared-secret
pre-shared-secret 123456
}
}
name-server 119.29.29.29
outside-address 192.168.66.108
}
}