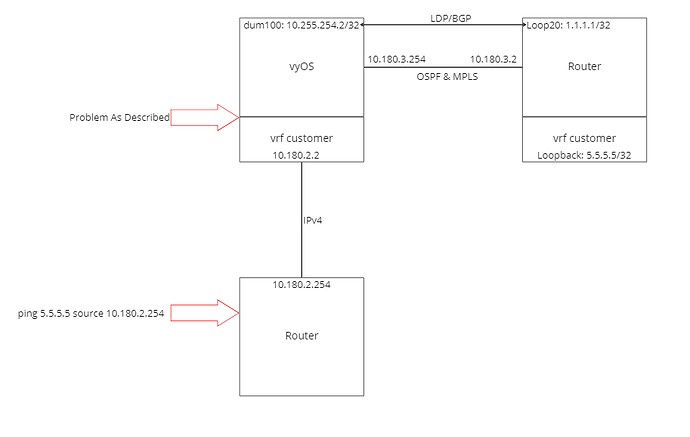
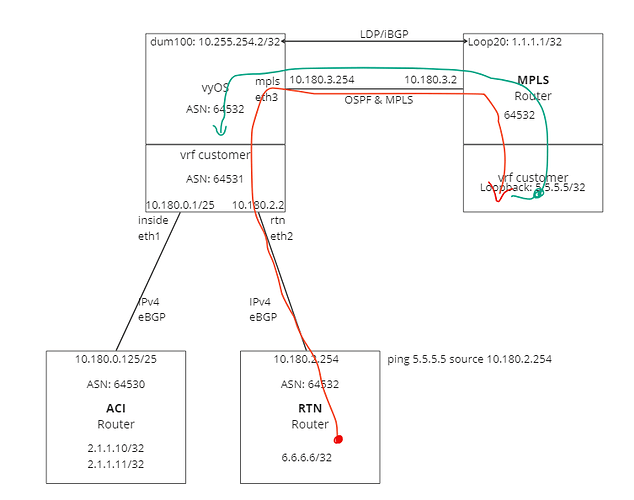
I have a problem with L3VPNs and specifically with the import/export of routes in/out of VRF. The exported route from the VRF is declared as ‘inaccessible’ due to the fact that the route has a next hop of the global route table BGP loopback, although the RIB correctly states it is in the ‘customer’ VRF.
[VyOS 1.4-rolling-202211180318] - sh ver below
The following output shows:
-
The route from within the VRF ‘customer’ which is correct and is in fact directly connected.
-
The route from after being exported into a L3VPN, which shows ‘inaccessible’ with the IP of 10.255.254.2, which is in fact in the GRT as the GRT BGP process loopback/router-id.
This L3VPN should be pointing to an address inside the VRF customer.
My config issue or bug ?
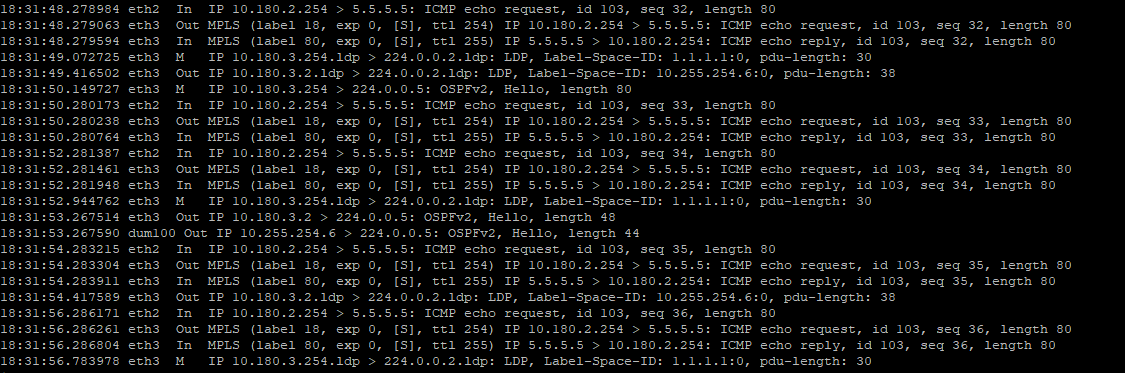
vyos@vyos-99:~$ **show bgp vrf customer ipv4 10.180.2.0/24**
BGP routing table entry for 10.180.2.0/24, version 1
Paths: (1 available, best #1, vrf customer)
Not advertised to any peer
Local
0.0.0.0 from 0.0.0.0 (10.180.2.2)
Origin IGP, metric 0, weight 32768, valid, sourced, local, best (First path received)
Last update: Thu Nov 24 16:32:16 2022
vyos@vyos-99:~$ **show bgp ipv4 vpn 10.180.2.0/24**
BGP routing table entry for 1:2:10.180.2.0/24, version 0
not allocated
Paths: (1 available, no best path)
Not advertised to any peer
Local
0.0.0.0 (**inaccessible**) from 0.0.0.0 (10.255.254.2) **vrf customer**(6) announce-nh-self
Origin IGP, metric 0, weight 32768, invalid, sourced, local
Extended Community: RT:2:1
Originator: 10.255.254.2
Remote label: 80
Last update: Thu Nov 24 17:10:15 2022
Topology
The version I am using is
Version: VyOS 1.4-rolling-202211180318
Release train: current
Built by: autobuild@vyos.net
Built on: Fri 18 Nov 2022 03:18 UTC
Build UUID: 7d903365-be97-4d56-865b-ca8560ae24aa
Build commit ID: 594c99e012fd66
Architecture: x86_64
Boot via: installed image
System type: VMware guest
Hardware vendor: VMware, Inc.
Hardware model: VMware Virtual Platform
Hardware S/N: VMware-42 08 c5 33 c1 d3 56 f5-83 1f 28 c4 b5 49 4d bc
Hardware UUID: 33c50842-d3c1-f556-831f-28c4b5494dbc
Copyright: VyOS maintainers and contributors
The configuration is:
interfaces {
dummy dum100 {
address 10.255.254.2/32
}
ethernet eth0 {
address 10.243.176.37/24
description MGMT
hw-id 00:50:56:88:36:22
offload {
gro
gso
sg
tso
}
vrf mgmt
}
ethernet eth1 {
address 10.180.0.1/25
description CUSTOMER
disable
hw-id 00:50:56:88:f2:d5
offload {
gro
gso
sg
tso
}
vrf customer
}
ethernet eth2 {
address 10.180.2.2/24
description RTN
hw-id 00:50:56:88:55:cd
offload {
gro
gso
sg
tso
}
vrf customer
}
ethernet eth3 {
address 10.180.3.2/24
description MPLS
hw-id 00:50:56:88:82:43
offload {
gro
gso
sg
tso
}
}
loopback lo {
}
}
protocols {
bgp {
neighbor 1.1.1.1 {
address-family {
ipv4-unicast {
}
ipv4-vpn {
soft-reconfiguration {
inbound
}
}
}
description "MPLS c8kv"
remote-as 64532
update-source 10.255.254.2
}
parameters {
log-neighbor-changes
router-id 10.255.254.2
}
system-as 64532
}
mpls {
interface eth3
ldp {
discovery {
transport-ipv4-address 10.255.254.2
}
export {
ipv4 {
explicit-null
}
}
interface eth3
router-id 10.255.254.2
}
}
ospf {
area 0 {
network 0.0.0.0/0
}
parameters {
abr-type cisco
router-id 10.255.254.2
}
}
}
service {
https {
api {
keys {
id REST {
key ****************
}
}
}
vrf mgmt
}
ssh {
client-keepalive-interval 180
listen-address 10.243.176.37
port 22
vrf mgmt
}
}
system {
config-management {
commit-revisions 100
}
conntrack {
modules {
ftp
h323
nfs
pptp
sip
sqlnet
tftp
}
}
domain-name prod.labs.haystacknetworks.com
host-name vyos-99
login {
banner {
post-login "EDP VRF Edge Security Appliance"
}
user vyos {
authentication {
encrypted-password ****************
}
}
}
name-server 192.168.10.1
name-server 192.168.1.20
ntp {
server 10.243.176.254 {
}
vrf mgmt
}
syslog {
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
}
vrf {
name customer {
protocols {
bgp {
address-family {
ipv4-unicast {
export {
vpn
}
import {
vpn
}
label {
vpn {
export auto
}
}
network 10.180.2.0/24 {
}
rd {
vpn {
export 1:2
}
}
route-target {
vpn {
export 2:1
import 1:1
}
}
}
}
neighbor 2.1.1.10 {
address-family {
ipv4-unicast {
nexthop-self {
}
soft-reconfiguration {
inbound
}
}
}
description "ACI L3out Customer Inside Loopback Peer A"
ebgp-multihop 3
remote-as 64530
update-source eth1
}
neighbor 2.1.1.11 {
address-family {
ipv4-unicast {
nexthop-self {
}
soft-reconfiguration {
inbound
}
}
}
description "ACI L3out Customer Inside Loopback Peer B"
ebgp-multihop 3
remote-as 64530
update-source eth1
}
parameters {
log-neighbor-changes
router-id 10.180.2.2
}
system-as 64531
}
static {
route 2.1.1.10/32 {
next-hop 10.180.0.125 {
}
}
route 2.1.1.11/32 {
next-hop 10.180.0.125 {
}
}
}
}
table 120
}
name mgmt {
protocols {
static {
route 0.0.0.0/0 {
next-hop 10.243.176.254 {
}
}
}
}
table 100
}
}