I removed all proxy IDs:
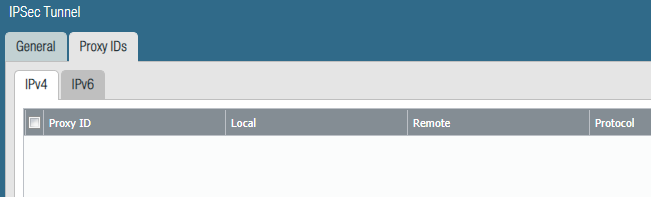
I don’t know where to add 0.0.0.0/0 for both remote and local subnets. Is that in the Virtual Routers?
I removed all proxy IDs:

I don’t know where to add 0.0.0.0/0 for both remote and local subnets. Is that in the Virtual Routers?
under virtual router keep the static routes as they were. In the IPsec tunnel IPv4 proxy id add an entry with 0.0.0.0/0 values for both local and remote
OK I added:
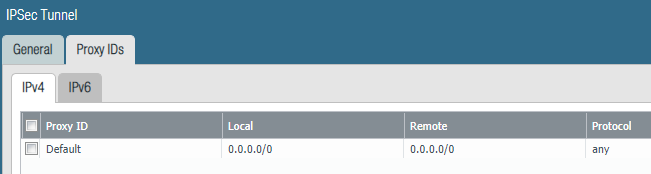
“under virtual router keep the static routes as they were” which setting you refer to please?
this one
yes correct, this routes
Still can’t ping peer hosts
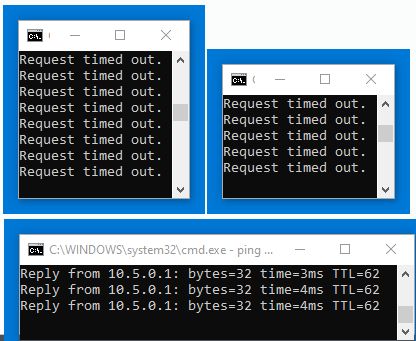
what is the IPsec tunnel status? Does it show UP?
In my setup everything works as expected with the same configuration. Try to restart vpn service on vyos running the command “restart vpn” and check again. I simplified Palo setup by allowing all traffic between all zones to ensure that there are no firewall rulles blocking anything.
I restarted the VPN and now, I can’t ping 10.5.0.1 anymore 
This setting is the culpit:
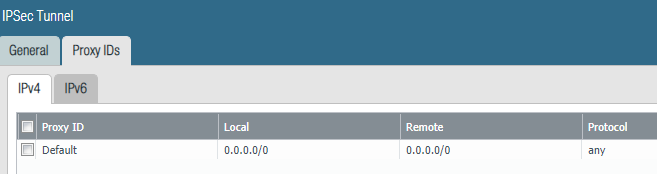
hm, what does the VPN status show?
show vpn ike sa
show vpn ipsec sa
show the VPN related config on VyOS:
show configuration commands | match vpn | strip-private
show configuration commands | match vti0 | strip-private
And also VPN configuration part on Palo
vyos@vpn-endpoint:~$ show configuration commands | match vpn | strip-private
set system host-name xxxxxx
set vpn ipsec esp-group vyos-pa-esp compression ‘disable’
set vpn ipsec esp-group vyos-pa-esp lifetime ‘3600’
set vpn ipsec esp-group vyos-pa-esp mode ‘tunnel’
set vpn ipsec esp-group vyos-pa-esp pfs ‘dh-group14’
set vpn ipsec esp-group vyos-pa-esp proposal 1 encryption ‘aes256gcm128’
set vpn ipsec esp-group vyos-pa-esp proposal 1 hash ‘sha256’
set vpn ipsec ike-group vyos-pa-ike close-action ‘none’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection action ‘clear’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection interval ‘30’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection timeout ‘90’
set vpn ipsec ike-group vyos-pa-ike ikev2-reauth ‘no’
set vpn ipsec ike-group vyos-pa-ike key-exchange ‘ikev2’
set vpn ipsec ike-group vyos-pa-ike lifetime ‘86400’
set vpn ipsec ike-group vyos-pa-ike proposal 1 dh-group ‘14’
set vpn ipsec ike-group vyos-pa-ike proposal 1 encryption ‘aes256’
set vpn ipsec ike-group vyos-pa-ike proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth0’
set vpn ipsec log level ‘2’
set vpn ipsec log subsystem ‘any’
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer xxxxx.tld authentication id ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer xxxxx.tld authentication pre-shared-secret xxxxxx
set vpn ipsec site-to-site peer xxxxx.tld authentication remote-id ‘xxx.xxx.10.66’
set vpn ipsec site-to-site peer xxxxx.tld connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxxx.tld default-esp-group ‘vyos-pa-esp’
set vpn ipsec site-to-site peer xxxxx.tld ike-group ‘vyos-pa-ike’
set vpn ipsec site-to-site peer xxxxx.tld ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxxx.tld local-address ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld vti bind ‘vti0’
set vpn ipsec site-to-site peer xxxxx.tld vti esp-group ‘vyos-pa-esp’
vyos@vpn-endpoint:~$ show configuration commands | match vti0 | strip-private
set interfaces vti vti0 address ‘xxx.xxx.255.254/30’
set interfaces vti vti0 description ‘pa-tunnel-address’
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/20 interface vti0
set protocols static route xxx.xxx.3.0/24 interface vti0
set vpn ipsec site-to-site peer xxxxx.tld vti bind ‘vti0’
so it’s more likely to be related:
From one of the previous screenshots it seems that there are no OUT packets on the VyOS tunnel side, so… maybe check the host-side network config? does it has a proper gateway pointing to the IP address configured on VyOS? Are there any defender/firewall settings enabled? Not sure what you can check more 
Here are my results:
vyos@Site-A:~$ show configuration commands | match vpn
set vpn ipsec esp-group vyos-pa-esp compression 'disable'
set vpn ipsec esp-group vyos-pa-esp lifetime '3600'
set vpn ipsec esp-group vyos-pa-esp mode 'tunnel'
set vpn ipsec esp-group vyos-pa-esp pfs 'dh-group14'
set vpn ipsec esp-group vyos-pa-esp proposal 1 encryption 'aes256'
set vpn ipsec esp-group vyos-pa-esp proposal 1 hash 'sha256'
set vpn ipsec ike-group vyos-pa-ike close-action 'none'
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection action 'restart'
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection interval '30'
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection timeout '90'
set vpn ipsec ike-group vyos-pa-ike ikev2-reauth 'no'
set vpn ipsec ike-group vyos-pa-ike key-exchange 'ikev1'
set vpn ipsec ike-group vyos-pa-ike lifetime '86400'
set vpn ipsec ike-group vyos-pa-ike proposal 1 dh-group '14'
set vpn ipsec ike-group vyos-pa-ike proposal 1 encryption 'aes256'
set vpn ipsec ike-group vyos-pa-ike proposal 1 hash 'sha256'
set vpn ipsec interface 'eth1'
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer 10.1.2.2 authentication id '10.1.1.2'
set vpn ipsec site-to-site peer 10.1.2.2 authentication mode 'pre-shared-secret'
set vpn ipsec site-to-site peer 10.1.2.2 authentication pre-shared-secret 'secret'
set vpn ipsec site-to-site peer 10.1.2.2 authentication remote-id '10.1.2.2'
set vpn ipsec site-to-site peer 10.1.2.2 connection-type 'initiate'
set vpn ipsec site-to-site peer 10.1.2.2 default-esp-group 'vyos-pa-esp'
set vpn ipsec site-to-site peer 10.1.2.2 ike-group 'vyos-pa-ike'
set vpn ipsec site-to-site peer 10.1.2.2 ikev2-reauth 'inherit'
set vpn ipsec site-to-site peer 10.1.2.2 local-address '10.1.1.2'
set vpn ipsec site-to-site peer 10.1.2.2 vti bind 'vti0'
set vpn ipsec site-to-site peer 10.1.2.2 vti esp-group 'vyos-pa-esp'
vyos@Site-A:~$ show configuration commands | match vti
set interfaces vti vti0 address '10.255.0.254/24'
set interfaces vti vti0 description 'pa-tunnel-address'
set protocols static route 10.10.0.0/20 interface vti0
set protocols static route 192.168.3.0/24 interface vti0
set vpn ipsec site-to-site peer 10.1.2.2 vti bind 'vti0'
set vpn ipsec site-to-site peer 10.1.2.2 vti esp-group 'vyos-pa-esp'
vyos@Site-A:~$ ping 192.168.3.11 source-address 192.168.2.1
PING 192.168.3.11 (192.168.3.11) from 192.168.2.1 : 56(84) bytes of data.
64 bytes from 192.168.3.11: icmp_seq=1 ttl=63 time=5.07 ms
64 bytes from 192.168.3.11: icmp_seq=2 ttl=63 time=6.73 ms
64 bytes from 192.168.3.11: icmp_seq=3 ttl=63 time=1.99 ms
64 bytes from 192.168.3.11: icmp_seq=4 ttl=63 time=7.99 ms
64 bytes from 192.168.3.11: icmp_seq=5 ttl=63 time=2.28 ms
^C
--- 192.168.3.11 ping statistics ---
5 packets transmitted, 5 received, 0% packet loss, time 4007ms
rtt min/avg/max/mdev = 1.988/4.810/7.986/2.375 ms
vyos@Site-A:~$ show vpn ipsec sa
Connection State Uptime Bytes In/Out Packets In/Out Remote address Remote ID Proposal
----------------- ------- -------- -------------- ---------------- ---------------- ----------- ---------------------------------------
peer_10-1-2-2_vti up 19m43s 420B/420B 5B/5B 10.1.2.2 10.1.2.2 AES_CBC_256/HMAC_SHA2_256_128/MODP_2048
Hi,
In my case it works like this:
set interfaces ethernet eth0 address ‘dhcp’
set interfaces ethernet eth0 description ‘OUTSIDE’
set interfaces ethernet eth0 hw-id ‘xx:xx:xx:xx:xx:d4’
set interfaces ethernet eth0 offload gro
set interfaces ethernet eth0 offload gso
set interfaces ethernet eth0 offload sg
set interfaces ethernet eth0 offload tso
set interfaces ethernet eth1 address ‘xxx.xxx.0.1/24’
set interfaces ethernet eth1 description ‘INSIDE’
set interfaces ethernet eth1 offload gro
set interfaces ethernet eth1 offload gso
set interfaces ethernet eth1 offload sg
set interfaces ethernet eth1 offload tso
set interfaces loopback lo
set interfaces vti vti0 address ‘xxx.xxx.0.254/24’
set interfaces vti vti0 description ‘pa-tunnel-address’
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/20 interface vti0
set protocols static route xxx.xxx.3.0/24 interface vti0
set service ssh client-keepalive-interval ‘180’
set service ssh port ‘22’
set system config-management commit-revisions ‘100’
set system conntrack modules ftp
set system conntrack modules h323
set system conntrack modules nfs
set system conntrack modules pptp
set system conntrack modules sip
set system conntrack modules sqlnet
set system conntrack modules tftp
set system host-name xxxxxx
set system login user xxxxxx authentication encrypted-password xxxxxx
set system login user xxxxxx authentication plaintext-password xxxxxx
set system login user xxxxxx authentication public-keys [email protected] key xxxxxx
set system login user xxxxxx authentication public-keys [email protected] type ssh-xxx
set system ntp server xxxxx.tld
set system ntp server xxxxx.tld
set system ntp server xxxxx.tld
set system syslog global facility all level ‘notice’
set system syslog global facility protocols level ‘debug’
set system time-zone ‘Europe/Zurich’
set vpn ipsec esp-group vyos-pa-esp compression ‘disable’
set vpn ipsec esp-group vyos-pa-esp lifetime ‘3600’
set vpn ipsec esp-group vyos-pa-esp mode ‘tunnel’
set vpn ipsec esp-group vyos-pa-esp pfs ‘dh-group14’
set vpn ipsec esp-group vyos-pa-esp proposal 1 encryption ‘aes256gcm128’
set vpn ipsec esp-group vyos-pa-esp proposal 1 hash ‘sha256’
set vpn ipsec ike-group vyos-pa-ike close-action ‘none’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection action ‘clear’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection interval ‘30’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection timeout ‘90’
set vpn ipsec ike-group vyos-pa-ike ikev2-reauth ‘no’
set vpn ipsec ike-group vyos-pa-ike key-exchange ‘ikev2’
set vpn ipsec ike-group vyos-pa-ike lifetime ‘86400’
set vpn ipsec ike-group vyos-pa-ike proposal 1 dh-group ‘14’
set vpn ipsec ike-group vyos-pa-ike proposal 1 encryption ‘aes256’
set vpn ipsec ike-group vyos-pa-ike proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth0’
set vpn ipsec log level ‘2’
set vpn ipsec log subsystem ‘any’
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer xxxxx.tld authentication id ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer xxxxx.tld authentication pre-shared-secret xxxxxx
set vpn ipsec site-to-site peer xxxxx.tld authentication remote-id ‘xxx.xxx.10.66’
set vpn ipsec site-to-site peer xxxxx.tld connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxxx.tld default-esp-group ‘vyos-pa-esp’
set vpn ipsec site-to-site peer xxxxx.tld ike-group ‘vyos-pa-ike’
set vpn ipsec site-to-site peer xxxxx.tld ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxxx.tld local-address ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld vti bind ‘vti0’
set vpn ipsec site-to-site peer xxxxx.tld vti esp-group ‘vyos-pa-esp’
I added too routes into hosts behind VyOS and it works now.
I don’t know why if I modify vti0 ip from eth1 subnet the tunnel doesn’t work. So I keep it in the same subnet and it works.
This topic was automatically closed 2 days after the last reply. New replies are no longer allowed.