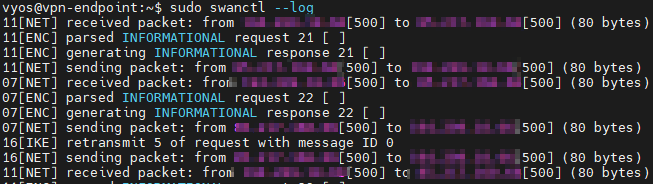
VyOS version: VyOS 1.4-rolling-202205250217
Hello,
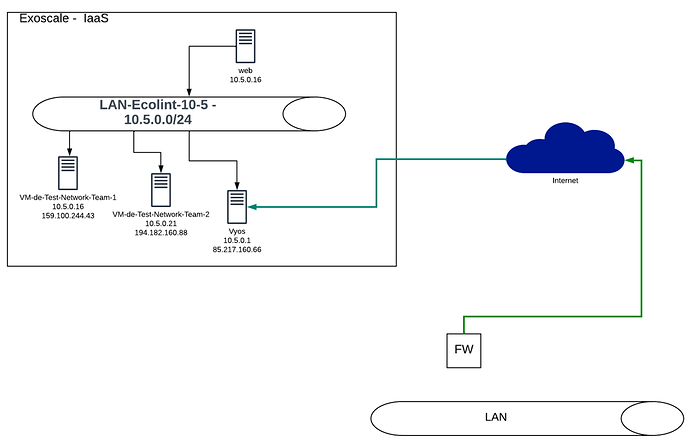
I setup a VyOS router and an ipsec tunnel between VyOS and my Firewall Palo Alto which works, the tunnel is up.
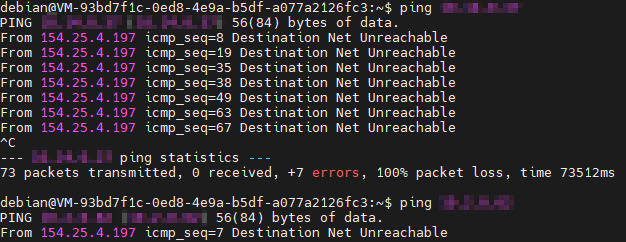
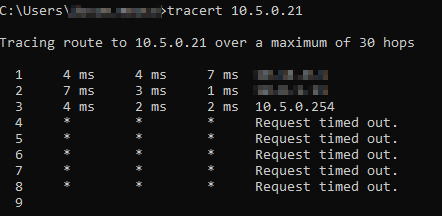
From my LAN I can ping the VyOS router but I cannot ping local clients.
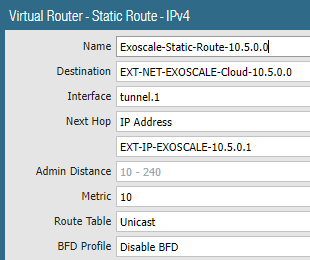
I setup the routes on both side, VyOS and Palo.
It worked for weeks and now suddenly it doesn’t work anymore.
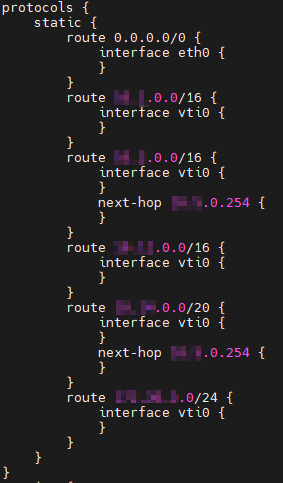
My VyOS config is as follows:
set interfaces ethernet eth0 address ‘dhcp’
set interfaces ethernet eth0 description ‘OUTSIDE’
set interfaces ethernet eth0 hw-id ‘xx:xx:xx:xx:xx:d4’
set interfaces ethernet eth0 offload gro
set interfaces ethernet eth0 offload gso
set interfaces ethernet eth0 offload sg
set interfaces ethernet eth0 offload tso
set interfaces ethernet eth1 address ‘xxx.xxx.0.1/24’
set interfaces ethernet eth1 description ‘INSIDE’
set interfaces ethernet eth1 offload gro
set interfaces ethernet eth1 offload gso
set interfaces ethernet eth1 offload sg
set interfaces ethernet eth1 offload tso
set interfaces loopback lo
set interfaces vti vti0 address ‘xxx.xxx.0.254/24’
set interfaces vti vti0 description ‘pa-tunnel-address’
set protocols static route xxx.xxx.0.0/0 interface eth0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/16 interface vti0
set protocols static route xxx.xxx.0.0/20 interface vti0
set protocols static route xxx.xxx.3.0/24 interface vti0
set service ssh client-keepalive-interval ‘180’
set service ssh port ‘22’
set system config-management commit-revisions ‘100’
set system conntrack modules ftp
set system conntrack modules h323
set system conntrack modules nfs
set system conntrack modules pptp
set system conntrack modules sip
set system conntrack modules sqlnet
set system conntrack modules tftp
set system host-name xxxxxx
set system login user xxxxxx authentication encrypted-password xxxxxx
set system login user xxxxxx authentication plaintext-password xxxxxx
set system login user xxxxxx authentication public-keys [email protected] key xxxxxx
set system login user xxxxxx authentication public-keys [email protected] type ssh-xxx
set system name-server ‘eth0’
set system ntp server xxxxx.tld
set system ntp server xxxxx.tld
set system ntp server xxxxx.tld
set system syslog global facility all level ‘notice’
set system syslog global facility protocols level ‘debug’
set system time-zone ‘Europe/Zurich’
set vpn ipsec esp-group vyos-pa-esp compression ‘disable’
set vpn ipsec esp-group vyos-pa-esp lifetime ‘3600’
set vpn ipsec esp-group vyos-pa-esp mode ‘tunnel’
set vpn ipsec esp-group vyos-pa-esp pfs ‘dh-group14’
set vpn ipsec esp-group vyos-pa-esp proposal 1 encryption ‘aes256gcm128’
set vpn ipsec esp-group vyos-pa-esp proposal 1 hash ‘sha256’
set vpn ipsec ike-group vyos-pa-ike close-action ‘none’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection action ‘clear’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection interval ‘30’
set vpn ipsec ike-group vyos-pa-ike dead-peer-detection timeout ‘90’
set vpn ipsec ike-group vyos-pa-ike ikev2-reauth ‘no’
set vpn ipsec ike-group vyos-pa-ike key-exchange ‘ikev2’
set vpn ipsec ike-group vyos-pa-ike lifetime ‘86400’
set vpn ipsec ike-group vyos-pa-ike proposal 1 dh-group ‘14’
set vpn ipsec ike-group vyos-pa-ike proposal 1 encryption ‘aes256’
set vpn ipsec ike-group vyos-pa-ike proposal 1 hash ‘sha256’
set vpn ipsec interface ‘eth0’
set vpn ipsec log level ‘2’
set vpn ipsec log subsystem ‘any’
set vpn ipsec options disable-route-autoinstall
set vpn ipsec site-to-site peer xxxxx.tld authentication id ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer xxxxx.tld authentication pre-shared-secret xxxxxx
set vpn ipsec site-to-site peer xxxxx.tld authentication remote-id ‘xxx.xxx.10.66’
set vpn ipsec site-to-site peer xxxxx.tld connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxxx.tld default-esp-group ‘vyos-pa-esp’
set vpn ipsec site-to-site peer xxxxx.tld ike-group ‘vyos-pa-ike’
set vpn ipsec site-to-site peer xxxxx.tld ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxxx.tld local-address ‘xxx.xxx.160.66’
set vpn ipsec site-to-site peer xxxxx.tld vti bind ‘vti0’
set vpn ipsec site-to-site peer xxxxx.tld vti esp-group ‘vyos-pa-esp’
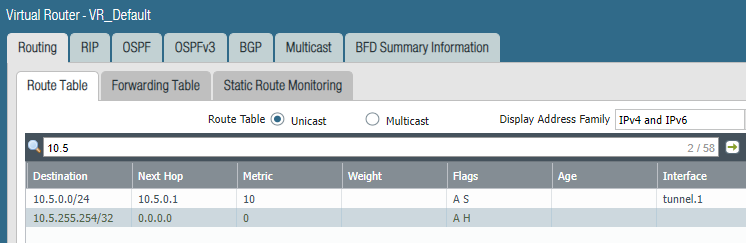
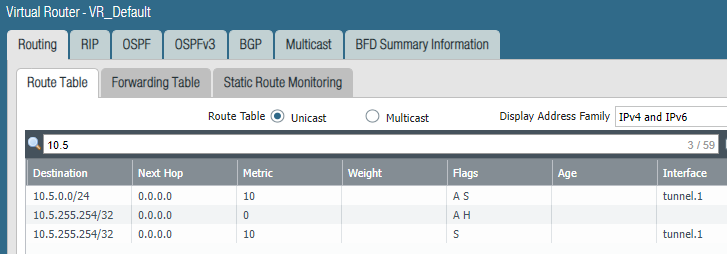
vyos@vpn-endpoint:~$ show ip route
S>* 0.0.0.0/0 [1/0] is directly connected, eth0, weight 1, 00:01:56
S 0.0.0.0/0 [210/0] via 85.217.160.1, eth0, weight 1, 00:01:58
S>* x.x.0.0/16 [1/0] is directly connected, vti0, weight 1, 00:01:56
S>* x.x.0.0/16 [1/0] is directly connected, vti0, weight 1, 00:01:56
C * x.x.0.0/24 is directly connected, vti0, 00:01:59
C>* x.x.0.0/24 is directly connected, eth1, 00:02:00
S>* x.x.0.0/16 [1/0] is directly connected, vti0, weight 1, 00:01:56
S>* x.x.0.0/20 [1/0] is directly connected, vti0, weight 1, 00:01:56
C>* x.x.x.x/23 is directly connected, eth0, 00:01:59
S>* x.x.x.0/24 [1/0] is directly connected, vti0, weight 1, 00:01:56
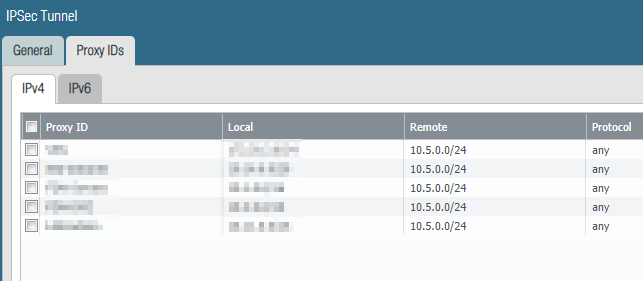
Palo Alto side:
<entry name="Tunnel-Exoscale">
<auto-key>
<ike-gateway>
<entry name="IKE_Gateway-Exoscale"/>
</ike-gateway>
<ipsec-crypto-profile>IPSec_Crypto-Exoscale-Phase2</ipsec-crypto-profile>
<proxy-id>
<entry name="xxx">
<protocol>
<any/>
</protocol>
<local>x.x.x.0/24</local>
<remote>x.x.0.254</remote>
</entry>
<entry name="xxx">
<protocol>
<any/>
</protocol>
<local>x.x.0.0/20</local>
<remote>x.x.0.254</remote>
</entry>
<entry name="xxx">
<protocol>
<any/>
</protocol>
<local>x.x.0.0/16</local>
<remote>x.x.0.254</remote>
</entry>
<entry name="xxx">
<protocol>
<any/>
</protocol>
<local>x.x.0.0/16</local>
<remote>x.x.0.254</remote>
</entry>
<entry name="xxx">
<protocol>
<any/>
</protocol>
<local>x.x.0.0/16</local>
<remote>x.x.0.254</remote>
</entry>
</proxy-id>
</auto-key>
<tunnel-monitor>
<enable>no</enable>
</tunnel-monitor>
<tunnel-interface>tunnel.1</tunnel-interface>
<disabled>no</disabled>
</entry>
</ipsec>
Do you know what is wrong?
Thank you for your help,
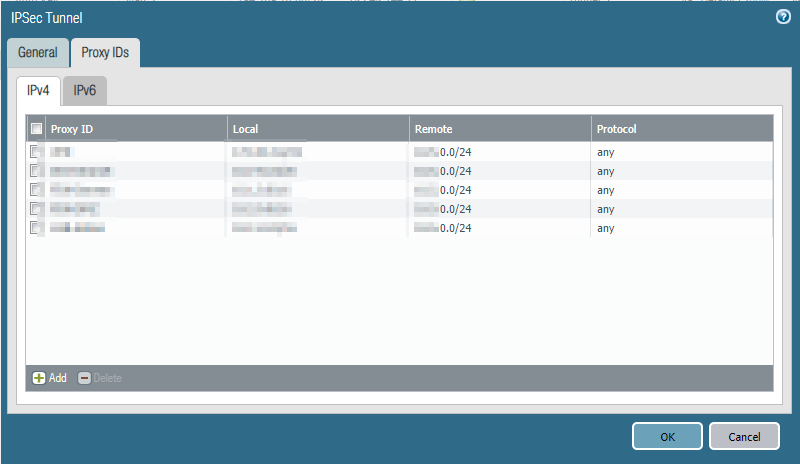
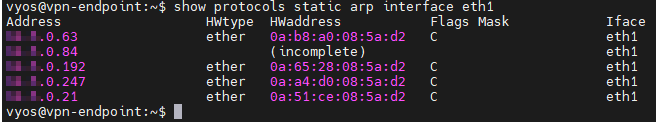
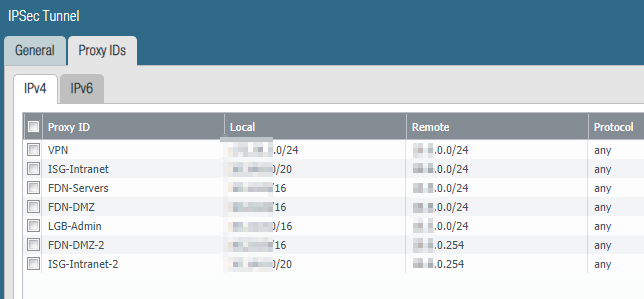
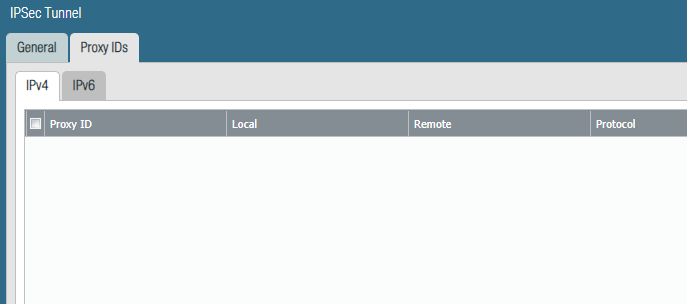
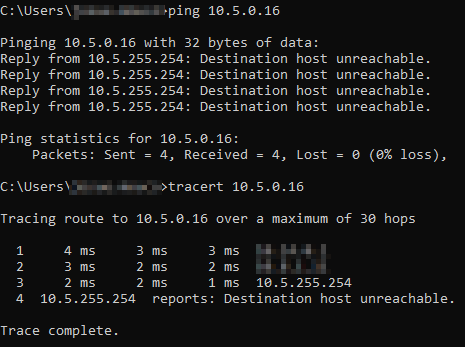
 So here is the last step you need to complete in order to get things work - bring back policy rules on your Palo that are containing the following:
So here is the last step you need to complete in order to get things work - bring back policy rules on your Palo that are containing the following: