Previously a have set up WAN load-balance with two ISP, this set up worked with no issues (during standby and failover) for a few years.
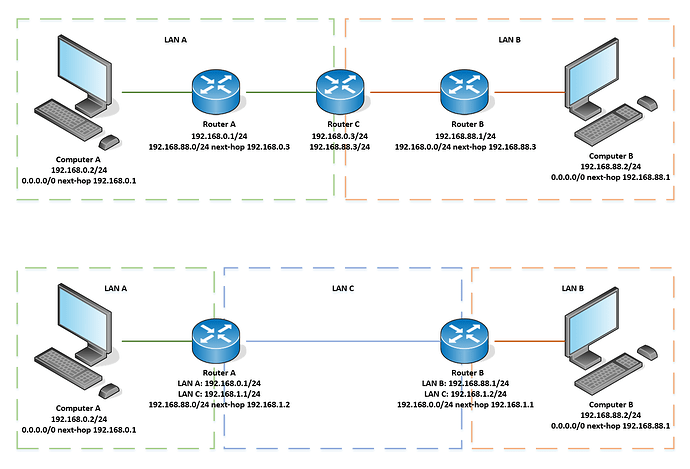
Now I want to connect my local network to another local network with a different subnet, as the router between subnets I use MikroTik, I’ve set up appropriate IPs on each of it interface, wipe out all default configurations related to firewall and bridge and now it can route between these two subnets without any restrictions. I’ve set up a static route in my VyOS router, checked routing - I can ping every device on the different subnet. But I can do it only from VyOS cli and not from the other local devices - for some reason when I do it from them I get a reply from my ISP gateway instead, so it looks like WAN load-balance ignores static route or has a higher priority.
I tried to alter the load-balance rule adding the subnet exclude option and created a separate higher priority rule with subnet exclude from load-balance, both of which solved the issue, I can ping devices between subnets successfully. But I can only ping them, I can’t reach MikroTik web interface for example.
When I set up the same static route on the computer everything works as expected, routing works like it should. So the root of the problem is definitely VyOS and its load-balance set up. Please help me figure out what I’m missing in the config.
Here is vyos config:
firewall {
all-ping enable
broadcast-ping disable
config-trap disable
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name WAN_IN {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
rule 20 {
action drop
state {
invalid enable
}
}
}
name WAN_LOCAL {
default-action drop
rule 10 {
action accept
state {
established enable
related enable
}
}
rule 20 {
action drop
state {
invalid enable
}
}
}
name WAN_OUT {
default-action accept
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
twa-hazards-protection disable
}
interfaces {
bridge br0 {
address 192.168.0.1/24
member {
interface eth0 {
}
interface eth1 {
}
}
}
ethernet eth0 {
hw-id xxx
}
ethernet eth1 {
hw-id xxx
}
ethernet eth2 {
address dhcp
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
out {
name WAN_OUT
}
}
hw-id xxx
}
ethernet eth3 {
address dhcp
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
out {
name WAN_OUT
}
}
hw-id xxx
}
loopback lo {
address 127.0.0.53/8
}
}
load-balancing {
wan {
enable-local-traffic
flush-connections
interface-health eth2 {
failure-count 5
nexthop dhcp
success-count 2
test 10 {
resp-time 5
target 1.1.1.1
ttl-limit 1
type ping
}
}
interface-health eth3 {
failure-count 5
nexthop dhcp
success-count 2
test 10 {
resp-time 5
target 1.0.0.1
ttl-limit 1
type ping
}
}
rule 10 {
destination {
address 1.1.1.1
}
inbound-interface lo
interface eth2 {
weight 1
}
protocol all
}
rule 20 {
destination {
address 1.0.0.1
}
inbound-interface lo
interface eth3 {
weight 1
}
protocol all
}
rule 25 {
destination {
address 192.168.88.0/24
}
exclude
inbound-interface br0
}
rule 30 {
failover
inbound-interface br0
interface eth2 {
weight 10
}
interface eth3 {
weight 1
}
protocol all
source {
address 192.168.0.201-192.168.0.254
}
}
rule 40 {
failover
inbound-interface br0
interface eth2 {
weight 1
}
interface eth3 {
weight 10
}
protocol all
source {
address 192.168.0.10-192.168.0.200
}
}
sticky-connections {
inbound
}
}
}
protocols {
static {
route 192.168.88.0/24 {
next-hop 192.168.0.5 {
}
}
}
}