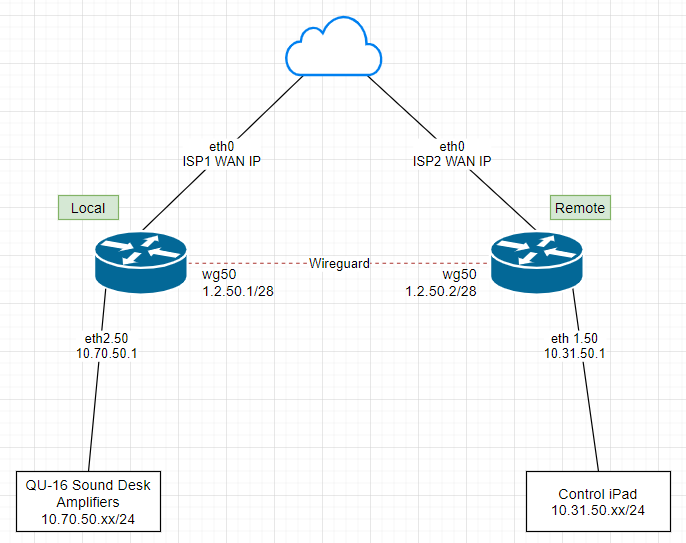
Hi all… I’m trying to get Wireguard working on Vyos 1.4, but I’m new to Vyos… and routing… and Wireguard… so probably just over my head.
What I’m trying to do is as follows:
My configs are below. At the moment, I can’t even ping either end of the tunnel from the respective routers, let alone route traffic over it… I’m guessing it might have something to do with firewall rules but I can’t figure what else is needed?
What are the tools/commands that I can use to debug a wireguard connection?
Thanks!
Local
local@vyos# run show wireguard keypairs pubkey default
***gnTo=
local@vyos# show interfaces wireguard
wireguard wg50 {
address 1.2.50.1/28
description MEDIA
peer Remote {
address {ISP2 WAN IP}
allowed-ips 10.31.50.0/24
allowed-ips 10.70.50.0/24
port 51820
pubkey ***aeTE=
}
port 51820
}
local@vyos# show firewall name WAN-LOCAL
default-action reject
rule 200 {
action accept
description "Wireguard 50 In"
destination {
port 51820
}
protocol udp
source {
address {ISP2 WAN IP}
}
}
local@vyos# show protocols static route
route 10.31.50.0/24 {
interface wg50 {
}
}
And on the Remote side
remote@vyos# run show wireguard keypairs pubkey default
***aeTE=
remote@vyos# show interfaces wireguard
wireguard wg50 {
address 1.2.50.2/28
description MEDIA
peer Local {
address {ISP1 WAN IP}
allowed-ips 10.70.50.0/24
allowed-ips 10.31.50.0/24
port 51820
pubkey ***gnTo=
}
port 51820
}
remote@vyos# show firewall name WAN-LOCAL
default-action drop
rule 200 {
action accept
description "Wireguard 50 In"
destination {
port 51820
}
protocol udp
source {
address {ISP1 WAN IP}
}
}
remote@vyos# show protocols static route
route 10.70.50.0/24 {
interface wg50 {
}
}