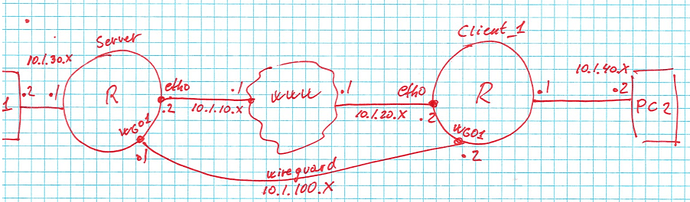
Can you ping from server 10.1.20.2?
Also, try to dump traffic on the wg01 interface. Do you see ICMP requests?
The first step, generate keys. On both nodes.
generate wireguard keypair
Take a close look at the keys and how they are located in the configuration on the routers.
vyos@left:~$ show wireguard pubkey
b4612Vv/jeL2DRT/YHFrFi+QxhBaKifIRj7ksg8PQS0=
vyos@left:~$
vyos@right:~$ show wireguard pubkey
unLicwlFoH2K1tgWJiep7H9YNW8pZmQ4UByJTDna4lY=
vyos@right:~$
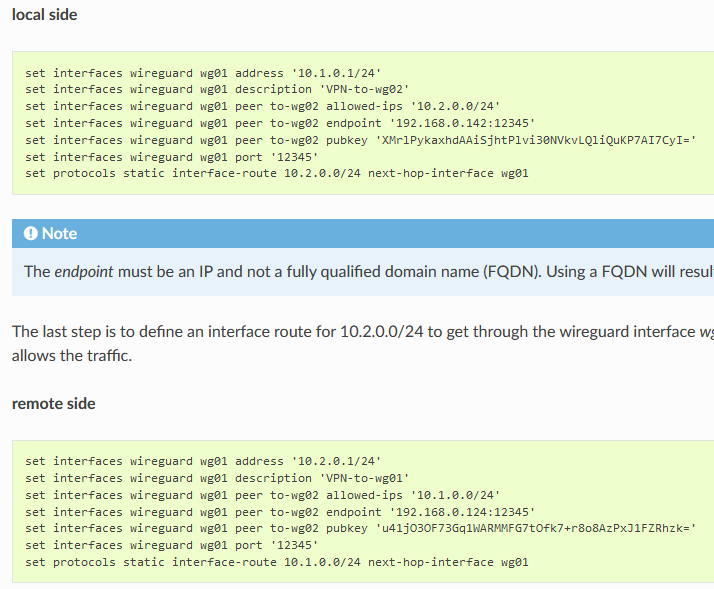
Config from the “left” node.
set interfaces ethernet eth0 address '10.1.10.2/24'
set interfaces wireguard wg1 address '10.1.100.1/30'
set interfaces wireguard wg1 description 'Client'
set interfaces wireguard wg1 peer PEER01 allowed-ips '10.1.100.0/24'
set interfaces wireguard wg1 peer PEER01 endpoint '10.1.20.2:12345'
set interfaces wireguard wg1 peer PEER01 pubkey 'unLicwlFoH2K1tgWJiep7H9YNW8pZmQ4UByJTDna4lY='
set interfaces wireguard wg1 port '12345'
set protocols static route 0.0.0.0/0 next-hop 10.1.10.1
set system host-name 'left'
Configuration from the “right” node
set interfaces ethernet eth0 address '10.1.20.2/24'
set interfaces wireguard wg1 address '10.1.100.2/30'
set interfaces wireguard wg1 description 'Server-SERVER-10.1.10.2'
set interfaces wireguard wg1 peer SERVER allowed-ips '10.1.100.0/24'
set interfaces wireguard wg1 peer SERVER endpoint '10.1.10.2:12345'
set interfaces wireguard wg1 peer SERVER pubkey 'b4612Vv/jeL2DRT/YHFrFi+QxhBaKifIRj7ksg8PQS0='
set interfaces wireguard wg1 port '12345'
set protocols static interface-route 10.1.100.0/24 next-hop-interface wg1
set protocols static route 0.0.0.0/0 next-hop 10.1.20.1
set system host-name 'right'
Ping from “left” node and dump from “right” node
vyos@left:~$ ping 10.1.100.2 count 2
PING 10.1.100.2 (10.1.100.2) 56(84) bytes of data.
64 bytes from 10.1.100.2: icmp_seq=1 ttl=64 time=7.79 ms
64 bytes from 10.1.100.2: icmp_seq=2 ttl=64 time=2.06 ms
--- 10.1.100.2 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1002ms
rtt min/avg/max/mdev = 2.065/4.932/7.799/2.867 ms
vyos@left:~$
vyos@right:~$ sudo tcpdump -ntvi wg1
tcpdump: listening on wg1, link-type RAW (Raw IP), capture size 262144 bytes
IP (tos 0x0, ttl 64, id 28118, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.100.1 > 10.1.100.2: ICMP echo request, id 4919, seq 1, length 64
IP (tos 0x0, ttl 64, id 43878, offset 0, flags [none], proto ICMP (1), length 84)
10.1.100.2 > 10.1.100.1: ICMP echo reply, id 4919, seq 1, length 64
IP (tos 0x0, ttl 64, id 28184, offset 0, flags [DF], proto ICMP (1), length 84)
10.1.100.1 > 10.1.100.2: ICMP echo request, id 4919, seq 2, length 64
IP (tos 0x0, ttl 64, id 44022, offset 0, flags [none], proto ICMP (1), length 84)
10.1.100.2 > 10.1.100.1: ICMP echo reply, id 4919, seq 2, length 64


 Ok
Ok