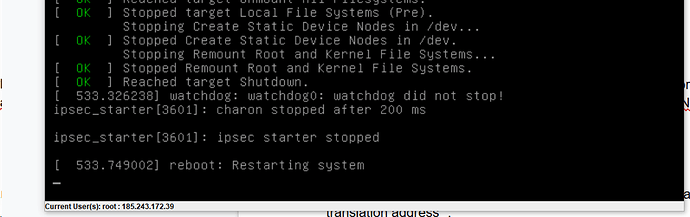
Hi, I have 1.20 installed on the Dell R220. When i type the reboot command, the server will end up on that line and the server will not reboot. Any ideas? in 1.18 is everythink OK
Are you using a rolling release, or did you build this from source? If rolling, what version?
no, its LTS…from subscribe iso… i use only stable versions
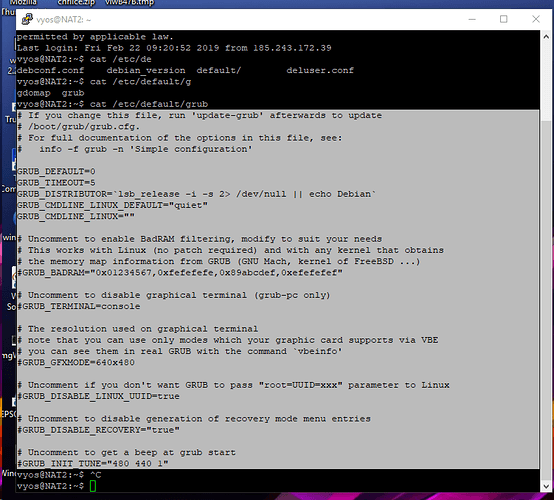
Can you provide me details of etc/default/grub?
Couple of options, toggle some ACPI (S1 states, etc) settings in bios to see if it impoves the behavior,
I’d only recommend doing the below on a machine you have phsyical access to and isn’t production:
modify:
GRUB_CMDLINE_LINUX_DEFAULT="quiet" <<replace "quiet" with "reboot=bios" or "reboot=pci quiet"
then:
sudo update-grub
then test to see if reboot is fixed.
eeh… /usr/sbin/grub-probe: error: failed to get canonical path of `overlay’.
Hmm…I’ve got a few R210II (About the same) that I run on, and I don’t see any isssues with rebooting. Have you had a chance to verify BIOS settings?
yes i check it…thank you
My apologies, grub-update isn’t actually an option. What bios version are you running on the R220?
last 1.10.3 version…
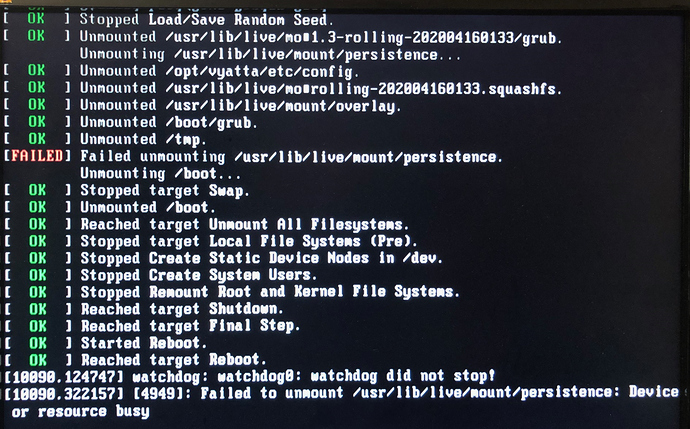
I have this same issue on a QOTOM Q190G4N-S07, the issue persists even after I have upgraded to 1.3. The reload hangs in the same spot which makes remote resets impossible. After upgrading to vyos-1.3-rolling-202002180217-amd64.iso, I get a failure condition during the reboot teardown process that reads " failed unmounting /usr/lib/live/mount/persistence…"
Do you have any insight into why this may be occurring or what I can do to make reboot work as intendend?
Thank you,
-Nathan
Hi @fajncba75 can you also open ticket via support@vyos.io on this issue.
Thanks!
@Net_Admin, can you add to ticket your configuration?
show configuration commands
Dmitry,
Sorry for the delay. Here is a sanitized version of my “show configuration commands”
host:~$ show configuration commands
set firewall all-ping ‘enable’
set firewall broadcast-ping ‘disable’
set firewall config-trap ‘disable’
set firewall group network-group xxxx network ‘x.x.x.x/x’
set firewall group network-group xxxx network ‘x.x.x.x/x’’
set firewall group network-group xxxx network ‘x.x.x.x/x’’
set firewall group network-group xxxx network ‘x.x.x.x/x’’
set firewall group network-group xxxx network ‘x.x.x.x’
set firewall ipv6-receive-redirects ‘disable’
set firewall ipv6-src-route ‘disable’
set firewall ip-src-route ‘disable’
set firewall log-martians ‘enable’
set firewall name OUTSIDE-IN default-action ‘drop’
set firewall name OUTSIDE-IN enable-default-log
set firewall name OUTSIDE-IN rule 10 action ‘accept’
set firewall name OUTSIDE-IN rule 10 state established ‘enable’
set firewall name OUTSIDE-IN rule 10 state related ‘enable’
set firewall name OUTSIDE-IN rule 20 action ‘accept’
set firewall name OUTSIDE-IN rule 20 destination port ‘xxxxx’
set firewall name OUTSIDE-IN rule 20 protocol ‘tcp’
set firewall name OUTSIDE-IN rule 20 source group network-group ‘xxxx’
set firewall name OUTSIDE-IN rule 20 state new ‘enable’
set firewall name OUTSIDE-LOCAL default-action ‘drop’
set firewall name OUTSIDE-LOCAL enable-default-log
set firewall name OUTSIDE-LOCAL rule 10 action ‘accept’
set firewall name OUTSIDE-LOCAL rule 10 state established ‘enable’
set firewall name OUTSIDE-LOCAL rule 10 state related ‘enable’
set firewall name OUTSIDE-LOCAL rule 20 action ‘accept’
set firewall name OUTSIDE-LOCAL rule 20 icmp type-name ‘echo-request’
set firewall name OUTSIDE-LOCAL rule 20 protocol ‘icmp’
set firewall name OUTSIDE-LOCAL rule 20 state new ‘enable’
set firewall name OUTSIDE-LOCAL rule 30 action ‘drop’
set firewall name OUTSIDE-LOCAL rule 30 destination port ‘xx’
set firewall name OUTSIDE-LOCAL rule 30 protocol ‘tcp’
set firewall name OUTSIDE-LOCAL rule 30 recent count ‘4’
set firewall name OUTSIDE-LOCAL rule 30 recent time ‘60’
set firewall name OUTSIDE-LOCAL rule 30 state new ‘enable’
set firewall name OUTSIDE-LOCAL rule 31 action ‘accept’
set firewall name OUTSIDE-LOCAL rule 31 destination port ‘xx’
set firewall name OUTSIDE-LOCAL rule 31 protocol ‘tcp’
set firewall name OUTSIDE-LOCAL rule 31 source address ‘x.x.x.x/x’
set firewall name OUTSIDE-LOCAL rule 31 state new ‘enable’
set firewall name OUTSIDE-LOCAL rule 32 action ‘accept’
set firewall name OUTSIDE-LOCAL rule 32 destination port ‘xxxx’
set firewall name OUTSIDE-LOCAL rule 32 protocol ‘udp’
set firewall name OUTSIDE-LOCAL rule 32 source group network-group ‘xxxx’
set firewall name OUTSIDE-LOCAL rule 32 state new ‘enable’
set firewall name OUTSIDE-LOCAL rule 33 action ‘accept’
set firewall name OUTSIDE-LOCAL rule 33 protocol ‘xx’
set firewall name OUTSIDE-LOCAL rule 33 source group network-group ‘xxxx’
set firewall name OUTSIDE-LOCAL rule 33 state new ‘enable’
set firewall name xxxx default-action ‘drop’
set firewall name xxxx enable-default-log
set firewall name xxxx rule 1000 action ‘accept’
set firewall name xxxx rule 1000 destination group network-group ‘xxxx’
set firewall name xxxx rule 1000 destination port ‘xxxx’
set firewall name xxxx rule 1000 protocol ‘tcp’
set firewall name xxxx rule 1000 source group network-group ‘xxxx’
set firewall name xxxx rule 1000 state established ‘enable’
set firewall name xxxx rule 1000 state new ‘enable’
set firewall name xxxx rule 1000 state related ‘enable’
set firewall name xxxx rule 1001 action ‘accept’
set firewall name xxxx rule 1001 destination group network-group ‘xxxx’
set firewall name xxxx rule 1001 destination port ‘xxxx’
set firewall name xxxx rule 1001 protocol ‘tcp’
set firewall name xxxx rule 1001 source group network-group ‘xxxx’
set firewall name xxxx rule 1001 state established ‘enable’
set firewall name xxxx rule 1001 state new ‘enable’
set firewall name xxxx rule 1001 state related ‘enable’
set firewall name xxxx rule 2000 action ‘accept’
set firewall name xxxx rule 2000 destination port ‘xx’
set firewall name xxxx rule 2000 protocol ‘tcp’
set firewall name xxxx rule 2000 source group network-group ‘xxxx’
set firewall receive-redirects ‘disable’
set firewall send-redirects ‘enable’
set firewall source-validation ‘disable’
set firewall syn-cookies ‘enable’
set firewall twa-hazards-protection ‘disable’
set interfaces ethernet eth0 address ‘x.x.x.x/x’
set interfaces ethernet eth0 description ‘OUTSIDE’
set interfaces ethernet eth0 firewall in name ‘OUTSIDE-IN’
set interfaces ethernet eth0 firewall local name ‘OUTSIDE-LOCAL’
set interfaces ethernet eth0 hw-id ‘x.x.x.x’
set interfaces ethernet eth1 address ‘x.x.x.x/x’
set interfaces ethernet eth1 description ‘xxxx’
set interfaces ethernet eth1 firewall local name ‘xxxx’
set interfaces ethernet eth1 hw-id ‘x.x.x.x’
set interfaces ethernet eth2 hw-id ‘x.x.x.x’
set interfaces ethernet eth3 hw-id ‘x.x.x.x’
set interfaces loopback lo
set protocols static route 0.0.0.0/0 next-hop x.x.x.x
set protocols static route 0.0.0.0/0 next-hop x.x.x.x
set service ssh key-exchange ‘diffie-hellman-groupxxx’
set service ssh key-exchange ‘diffie-hellman-group-exchange-xxx’
set service ssh listen-address 'x.x.x.x
set service ssh listen-address ‘x.x.x.x’
set service ssh port ‘xxxx’
set system config-management commit-revisions ‘100’
set system conntrack expect-table-size ‘2048’
set system conntrack hash-size ‘32768’
set system conntrack table-size ‘262144’
set system console device ttyS0 speed ‘115200’
set system host-name ‘Host’
set system login user xxxx authentication encrypted-password ‘xxxx’
set system login user xxxx authentication plaintext-password ‘’
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system ntp server xxxx
set system ntp server xxxx
set system syslog global facility all level ‘info’
set system syslog global facility protocols level ‘debug’
set system time-zone ‘UTC’
set vpn ipsec esp-group xxxx-esp compression ‘disable’
set vpn ipsec esp-group xxxx-esp lifetime ‘1800’
set vpn ipsec esp-group xxxx-esp mode ‘tunnel’
set vpn ipsec esp-group xxxx-esp pfs ‘disable’
set vpn ipsec esp-group xxxx-esp proposal 1 encryption ‘xxxxxx’
set vpn ipsec esp-group xxxx-esp proposal 1 hash ‘xxx’
set vpn ipsec ike-group xxxx_ike close-action ‘none’
set vpn ipsec ike-group xxxx_ike ikev2-reauth ‘no’
set vpn ipsec ike-group xxxx_ike key-exchange ‘x’
set vpn ipsec ike-group xxxx_ike lifetime ‘3600’
set vpn ipsec ike-group xxxx_ike proposal 1 dh-group ‘2’
set vpn ipsec ike-group xxxx_ike proposal 1 encryption ‘x’
set vpn ipsec ike-group xxxx_ike proposal 1 hash ‘x’
set vpn ipsec ipsec-interfaces interface ‘eth0’
set vpn ipsec site-to-site peer x.x.x.x authentication mode ‘pre-shared-secret’
set vpn ipsec site-to-site peer x.x.x.x authentication pre-shared-secret ‘xxxx’
set vpn ipsec site-to-site peer xxxx connection-type ‘initiate’
set vpn ipsec site-to-site peer xxxx ike-group ‘xxx’
set vpn ipsec site-to-site peer xxxx ikev2-reauth ‘inherit’
set vpn ipsec site-to-site peer xxxx local-address ‘xxxx’
set vpn ipsec site-to-site peer xxxx tunnel 1 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer xxxx tunnel 1 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer xxxx tunnel 1 esp-group ‘xxxx-esp’
set vpn ipsec site-to-site peer x.x.x.x tunnel 1 local prefix ‘xxxx’
set vpn ipsec site-to-site peer x.x.x.x tunnel 1 remote prefix ‘xxxx’
set vpn ipsec site-to-site peer x.x.x.x tunnel 2 allow-nat-networks ‘disable’
set vpn ipsec site-to-site peer x.x.x.x tunnel 2 allow-public-networks ‘disable’
set vpn ipsec site-to-site peer x.x.x.x tunnel 2 esp-group ‘xxxx’
set vpn ipsec site-to-site peer x.x.x.x tunnel 2 local prefix ‘xxxx’
set vpn ipsec site-to-site peer x.x.x.x tunnel 2 remote prefix ‘xxxx’
How does this play into the boot process? I appreciate your insight.
-Nathan
Hello, @Net_Admin
I can’t reproduce this issue on my test router with your config. Can you capture video from the console when router reboots?
Dmitry,
Sorry for the delay.
Here is the image of the error condition. The device just hangs here on reboot.
Hi @Nathan, you can try to use a dirty hook, edit /etc/systemd/system.conf and add
ShutdownWatchdogSec=1min
I believe better find this issue, but this does not reproducible in our LAB
Hi @Dmitry, I have the exact same error on a vanilla VyOS installation. Except on my device I get no watchdog: watchdog0: watchdog did not stop! line. I’m using a Intel J1900 based mini-pc manufactured by XCY (model: X33 router).
The configuration on my device is:
set interface ethernet eth0 hw-id '00:c0:b7:e0:a2'
set interface ethernet eth1 hw-id '00:c0:b7:e0:a3'
set interface ethernet eth2 hw-id '00:c0:b7:e0:a4'
set interface ethernet eth3 hw-id '00:c0:b7:e0:a5'
set interface loopback lo
set system config-management commit-revisions '100'
set system console device ttyS0 speed '115200'
set system host-name 'vyos'
set system login user 'vyos' authentication encrypted-password 'HASH'
set system login user vyos authentication plaintext-password ''
set system ntp server 0.pool.ntp.org
set system ntp server 1.pool.ntp.org
set system ntp server 2.pool.ntp.org
set system syslog global facility all level 'info'
set system syslog global facility protocols level 'debug'
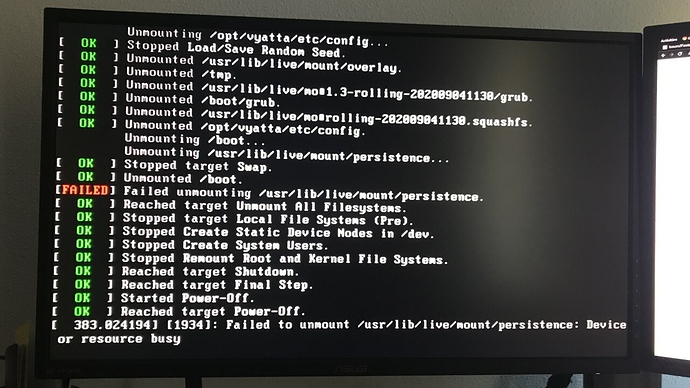
When initiating the poweroff command is get this screen and it freezes here until I hard poweroff the device by holding down the power button.
Also, after applying the suggested fix to the /etc/systemd/system.conf my behaviour matched the OP reported behaviour. The output now includes a watchdog: watchdog0: watchdog did not stop! line.