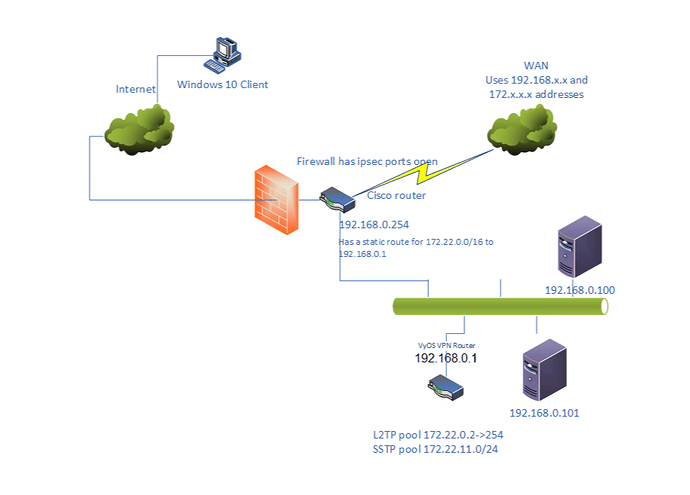
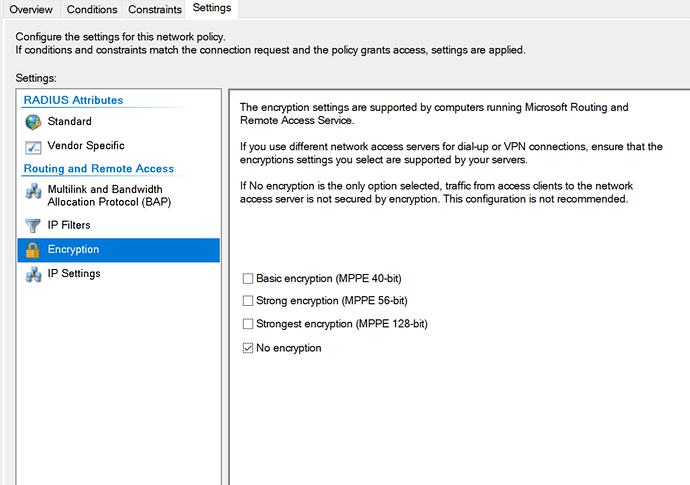
I have been getting L2TP and SSTP to work with local authentication and I have also been following this thread: IPSEC/L2TP with RADIUS on WIN2019 Server - Need help - #21 by hook.ua
I did have very similar problems with local authentication and did solve it by adding mppe=deny for both l2tp and ppp (I have now also added ccp=0, but I don’t think that really does any change when mppe=deny has been set). Worth noticing is that chaninging mppe to deny in the Vyos config does not change it in the actual configuration files.
My main problem now is when I add radius authentication (also Windows 2019 server NPS as radius). To simplify and show the difference I have modified the local /run/accel-pppd/l2tp.conf to have all configuration with only the “radius” module commented out in one case and the “chap-secretes” section commented in the other case.
Between the changes to the file the only other thing done is accel-cmd restart -p 2004
With local authentication everything works fine. I do get an IP-address, the connection works and I can reach resources on the local network. On the VyOS box I can run ifconfig and do get the configuration for l2tp0 as below:
l2tp0: flags=4305<UP,POINTOPOINT,RUNNING,NOARP,MULTICAST> mtu 1400
inet 10.255.255.0 netmask 255.255.255.255 destination 172.22.0.0
ppp txqueuelen 3 (Point-to-Point Protocol)
RX packets 219 bytes 20860 (20.3 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 188 bytes 83951 (81.9 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
When I enable radius the connection is established, I do get an IP-address, but the connection does not pass any traffic. Looking at ifconfig on the box will not show the l2tp0 interface unless I add “-a” and then the output is as below - there is no ipaddress or destination assigned.
l2tp0: flags=4240<POINTOPOINT,NOARP,MULTICAST> mtu 1400
ppp txqueuelen 3 (Point-to-Point Protocol)
RX packets 70 bytes 5202 (5.0 KiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4 bytes 70 (70.0 B)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
I have tested to change every possible option on the radius server for ip address assignment, but it does not make any difference (and since I actually get an ip-address for the client I don’t think that this is the problem).
I am running VyOS 1.3-rolling-202006160117
Below are masked configuration files and log extracts:
Config file
generated by accel_l2tp.py
[modules]
log_syslog
l2tp
chap-secrets
auth_mschap_v2
— Uncomment to test radius
#radius
ippool
shaper
ipv6pool
ipv6_nd
ipv6_dhcp
[core]
thread-count=2
[log]
syslog=accel-l2tp,daemon
copy=1
level=5
[dns]
dns1=x.x.96.74
dns2=x.x.96.35
[l2tp]
verbose=1
ifname=l2tp%d
ppp-max-mtu=1436
mppe=deny
ccp=0
bind=x.x.96.14
[client-ip-range]
0.0.0.0/0
[ip-pool]
172.22.0.0/16
gw-ip-address=10.255.255.0
Comment below section for radius mode
[chap-secrets]
chap-secrets=/run/accel-pppd/sstp.chap-secrets
gw-ip-address=10.255.255.0
[radius]
gw-ip-address=10.255.255.0
verbose=1
server=x.x.96.60,MyBigSecret,auth-port=1812,req-limit=0,fail-time=0
acct-timeout=3
timeout=300
max-try=3
nas-identifier=x.x.96.14
gw-ip-address=10.255.255.0
[ppp]
mppe=deny
ccp=0
verbose=1
check-ip=1
single-session=replace
lcp-echo-timeout=0
lcp-echo-interval=30
lcp-echo-failure=3
[cli]
tcp=127.0.0.1:2004
LOG FILE
First attempt is with local authentication, the second attempt is with Radius - masked out sensitive info
Jun 16 08:45:12 vyos accel-l2tp: terminate, sig = 15
Jun 16 08:45:12 vyos accel-l2tp: l2tp0:mylocaluser: send [LCP TermReq id=204]
Jun 16 08:45:12 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:45:12 vyos accel-l2tp: l2tp0:mylocaluser: recv [LCP TermAck id=cc]
Jun 16 08:45:12 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:45:12 vyos accel-l2tp: l2tp session 37009-13, 44069-1: data channel closed, disconnecting session
Jun 16 08:45:12 vyos accel-l2tp: l2tp session 37009-13, 44069-1: sending CDN (res: 2, err: 0)
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): send [L2TP tid=13 sid=1 Ns=13 Nr=4 <Assigned-Session-ID -21467> ]
Jun 16 08:45:12 vyos accel-l2tp: l2tp0:: session destroyed
Jun 16 08:45:12 vyos accel-l2tp: l2tp session 37009-13, 44069-1: deleting session
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): no more session, disconnecting tunnel
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): sending StopCCN (res: 1, err: 0)
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): send [L2TP tid=13 sid=0 Ns=14 Nr=4 <Assigned-Tunnel-ID -28527> ]
Jun 16 08:45:12 vyos accel-l2tp: l2tp session 37009-13, 44069-1: session destroyed
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): context thread is closing, disconnecting tunnel
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): tunnel disconnection acknowledged by peer, deleting tunnel
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): deleting tunnel
Jun 16 08:45:12 vyos accel-l2tp: l2tp tunnel 37009-13 (x.x.217.67:1701): tunnel destroyed
Jun 16 08:45:13 vyos accel-l2tp: l2tp: iprange module disabled, improper IP configuration of PPP interfaces may cause kernel soft lockup
Jun 16 08:45:14 vyos ntpd[1476]: Deleting interface #6 l2tp0, 10.255.255.0#123, interface stats: received=0, sent=0, dropped=0, active_time=661 secs
Jun 16 08:45:56 vyos charon: 11[NET] received packet: from x.x.217.67[500] to y.y.96.14[500] (408 bytes)
Jun 16 08:45:56 vyos charon: 11[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V ]
Jun 16 08:45:56 vyos charon: 11[ENC] received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
Jun 16 08:45:56 vyos charon: 11[IKE] received MS NT5 ISAKMPOAKLEY vendor ID
Jun 16 08:45:56 vyos charon: 11[IKE] received NAT-T (RFC 3947) vendor ID
Jun 16 08:45:56 vyos charon: 11[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Jun 16 08:45:56 vyos charon: 11[IKE] received FRAGMENTATION vendor ID
Jun 16 08:45:56 vyos charon: 11[ENC] received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
Jun 16 08:45:56 vyos charon: 11[ENC] received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
Jun 16 08:45:56 vyos charon: 11[ENC] received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
Jun 16 08:45:56 vyos charon: 11[IKE] x.x.217.67 is initiating a Main Mode IKE_SA
Jun 16 08:45:56 vyos charon: 11[CFG] selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jun 16 08:45:56 vyos charon: 11[ENC] generating ID_PROT response 0 [ SA V V V V ]
Jun 16 08:45:56 vyos charon: 11[NET] sending packet: from y.y.96.14[500] to x.x.217.67[500] (156 bytes)
Jun 16 08:45:56 vyos charon: 10[NET] received packet: from x.x.217.67[500] to y.y.96.14[500] (260 bytes)
Jun 16 08:45:56 vyos charon: 10[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
Jun 16 08:45:56 vyos charon: 10[IKE] remote host is behind NAT
Jun 16 08:45:56 vyos charon: 10[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
Jun 16 08:45:56 vyos charon: 10[NET] sending packet: from y.y.96.14[500] to x.x.217.67[500] (244 bytes)
Jun 16 08:45:56 vyos charon: 12[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (68 bytes)
Jun 16 08:45:56 vyos charon: 12[ENC] parsed ID_PROT request 0 [ ID HASH ]
Jun 16 08:45:56 vyos charon: 12[CFG] looking for pre-shared key peer configs matching y.y.96.14…x.x.217.67[192.168.2.88]
Jun 16 08:45:56 vyos charon: 12[CFG] selected peer config “remote-access”
Jun 16 08:45:56 vyos charon: 12[IKE] detected reauth of existing IKE_SA, adopting 1 children and 0 virtual IPs
Jun 16 08:45:56 vyos charon: 12[IKE] schedule delete of duplicate IKE_SA for peer ‘192.168.2.88’ due to uniqueness policy and suspected reauthentication
Jun 16 08:45:56 vyos charon: 12[IKE] IKE_SA remote-access[7] established between y.y.96.14[y.y.96.14]…x.x.217.67[192.168.2.88]
Jun 16 08:45:56 vyos charon: 12[IKE] DPD not supported by peer, disabled
Jun 16 08:45:56 vyos charon: 12[ENC] generating ID_PROT response 0 [ ID HASH ]
Jun 16 08:45:56 vyos charon: 12[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (68 bytes)
Jun 16 08:45:56 vyos charon: 14[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (436 bytes)
Jun 16 08:45:56 vyos charon: 14[ENC] parsed QUICK_MODE request 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
Jun 16 08:45:56 vyos charon: 14[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Jun 16 08:45:56 vyos charon: 14[IKE] received 3600s lifetime, configured 0s
Jun 16 08:45:56 vyos charon: 14[IKE] received 250000000 lifebytes, configured 0
Jun 16 08:45:56 vyos charon: 14[IKE] detected rekeying of CHILD_SA remote-access{6}
Jun 16 08:45:56 vyos charon: 14[ENC] generating QUICK_MODE response 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
Jun 16 08:45:56 vyos charon: 14[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (204 bytes)
Jun 16 08:45:56 vyos charon: 15[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (60 bytes)
Jun 16 08:45:56 vyos charon: 15[ENC] parsed QUICK_MODE request 1 [ HASH ]
Jun 16 08:45:56 vyos charon: 15[IKE] CHILD_SA remote-access{7} established with SPIs cb76f6d5_i 65b1e758_o and TS y.y.96.14/32[udp/l2f] === x.x.217.67/32[udp/l2f]
Jun 16 08:45:56 vyos accel-l2tp: l2tp: recv [L2TP tid=0 sid=0 Ns=0 Nr=0 <Protocol-Version 256> <Framing-Capabilities 1> <Bearer-Capabilities 0> <Firmware-Revision 2560> <Assigned-Tunnel-ID 14> <Recv-Window-Size 8>]
Jun 16 08:45:56 vyos accel-l2tp: l2tp: handling SCCRQ from x.x.217.67
Jun 16 08:45:56 vyos accel-l2tp: l2tp: new tunnel 9959-14 created following reception of SCCRQ from x.x.217.67:1701
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): sending SCCRP
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): send [L2TP tid=14 sid=0 Ns=0 Nr=1 <Protocol-Version 256> <Framing-Capabilities 1> <Assigned-Tunnel-ID 9959> <Recv-Window-Size 16>]
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): recv [L2TP tid=9959 sid=0 Ns=1 Nr=1 ]
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): handling SCCCN
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): established at y.y.96.14:1701
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): recv [L2TP tid=9959 sid=0 Ns=2 Nr=1 <Assigned-Session-ID 1> <Call-Serial-Number 0> <Bearer-Type 2>]
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): handling ICRQ
Jun 16 08:45:56 vyos accel-l2tp: l2tp session 9959-14, 2537-1: sending ICRP
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): new session 2537-1 created following reception of ICRQ
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): send [L2TP tid=14 sid=1 Ns=1 Nr=3 <Assigned-Session-ID 2537>]
Jun 16 08:45:56 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): recv [L2TP tid=9959 sid=2537 Ns=3 Nr=2 <TX-Speed 400000000> <Framing-Type 1> <Proxy-Authen-Type 4>]
Jun 16 08:45:56 vyos accel-l2tp: l2tp session 9959-14, 2537-1: handling ICCN
Jun 16 08:45:56 vyos accel-l2tp: :: starting data channel for l2tp(x.x.217.67:1701 session 9959-14, 2537-1)
Jun 16 08:45:56 vyos accel-l2tp: :: send [LCP ConfReq id=7d <mru 1436> <magic 61ea223e>]
Jun 16 08:45:56 vyos accel-l2tp: :: recv [LCP ConfReq id=0 <mru 1400> <magic 5a47421a> ]
Jun 16 08:45:56 vyos accel-l2tp: :: send [LCP ConfRej id=0 ]
Jun 16 08:45:56 vyos accel-l2tp: :: recv [LCP ConfReq id=1 <mru 1400> <magic 5a47421a>]
Jun 16 08:45:56 vyos accel-l2tp: :: send [LCP ConfAck id=1 ]
Jun 16 08:45:59 vyos accel-l2tp: :: send [LCP ConfReq id=7d <mru 1436> <magic 61ea223e>]
Jun 16 08:45:59 vyos accel-l2tp: :: recv [LCP ConfAck id=7d <mru 1436> <magic 61ea223e>]
Jun 16 08:45:59 vyos accel-l2tp: :: send [MSCHAP-v2 Challenge id=1 <8d18d1a58aa9e1d48297de7284723437>]
Jun 16 08:45:59 vyos accel-l2tp: :: recv [MSCHAP-v2 Response id=1 , <7c18df3277824e0e2f6a265f5c19858ff7933b672ee22>, F=0, name=“mylocaluser”]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: connect: ppp0 ↔ l2tp(x.x.217.67:1701 session 9959-14, 2537-1)
Jun 16 08:45:59 vyos netplugd[986]: ppp0: ignoring event
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [MSCHAP-v2 Success id=1 “S=968856B8F73E91EAD9FDA2EE9D23D16CB1BBE71B M=Authentication succeeded”]
Jun 16 08:45:59 vyos netplugd[986]: ppp0: ignoring event
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: mylocaluser: authentication succeeded
Jun 16 08:45:59 vyos systemd-udevd[3119]: link_config: autonegotiation is unset or enabled, the speed and duplex are not writable.
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: IPV6CP: discarding packet
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [LCP ProtoRej id=127 <8057>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: CCP: discarding packet
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [LCP ProtoRej id=128 <80fd>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: recv [IPCP ConfReq id=4 <addr 0.0.0.0> <dns1 0.0.0.0> <wins1 0.0.0.0> <dns2 0.0.0.0> <wins2 0.0.0.0>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [IPCP ConfReq id=a0 <addr 10.255.255.0>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [IPCP ConfRej id=4 <wins1 0.0.0.0> <wins2 0.0.0.0>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: recv [IPCP ConfAck id=a0 <addr 10.255.255.0>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: recv [IPCP ConfReq id=5 <addr 0.0.0.0> <dns1 0.0.0.0> <dns2 0.0.0.0>]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [IPCP ConfNak id=5 <addr 172.22.0.0> ]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: recv [IPCP ConfReq id=6 <addr 172.22.0.0> ]
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: send [IPCP ConfAck id=6]
Jun 16 08:45:59 vyos kernel: [ 2672.619816] l2tp0: renamed from ppp0
Jun 16 08:45:59 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:45:59 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:45:59 vyos accel-l2tp: ppp0:mylocaluser: rename interface to ‘l2tp0’
Jun 16 08:45:59 vyos accel-l2tp: l2tp0:mylocaluser: session started over l2tp session 9959-14, 2537-1
Jun 16 08:46:00 vyos ntpd[1476]: Listen normally on 7 l2tp0 10.255.255.0:123
Jun 16 08:46:06 vyos charon: 13[IKE] deleting IKE_SA remote-access[6] between y.y.96.14[y.y.96.14]…x.x.217.67[192.168.2.88]
Jun 16 08:46:06 vyos charon: 13[IKE] sending DELETE for IKE_SA remote-access[6]
Jun 16 08:46:06 vyos charon: 13[ENC] generating INFORMATIONAL_V1 request 4078688329 [ HASH D ]
Jun 16 08:46:06 vyos charon: 13[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (84 bytes)
Jun 16 08:49:21 vyos accel-l2tp: cli: tcp: new connection from 127.0.0.1
Jun 16 08:49:21 vyos accel-l2tp: terminate, sig = 15
Jun 16 08:49:21 vyos accel-l2tp: l2tp0:mylocaluser: send [LCP TermReq id=135]
Jun 16 08:49:21 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:49:21 vyos accel-l2tp: l2tp0:mylocaluser: recv [LCP TermAck id=87]
Jun 16 08:49:21 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:49:21 vyos accel-l2tp: l2tp session 9959-14, 2537-1: data channel closed, disconnecting session
Jun 16 08:49:21 vyos accel-l2tp: l2tp session 9959-14, 2537-1: sending CDN (res: 2, err: 0)
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): send [L2TP tid=14 sid=1 Ns=5 Nr=4 <Assigned-Session-ID 2537> ]
Jun 16 08:49:21 vyos accel-l2tp: l2tp0:: session destroyed
Jun 16 08:49:21 vyos accel-l2tp: l2tp session 9959-14, 2537-1: deleting session
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): no more session, disconnecting tunnel
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): sending StopCCN (res: 1, err: 0)
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): send [L2TP tid=14 sid=0 Ns=6 Nr=4 <Assigned-Tunnel-ID 9959> ]
Jun 16 08:49:21 vyos accel-l2tp: l2tp session 9959-14, 2537-1: session destroyed
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): context thread is closing, disconnecting tunnel
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): discarding message received while disconnecting
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): tunnel disconnection acknowledged by peer, deleting tunnel
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): deleting tunnel
Jun 16 08:49:21 vyos accel-l2tp: l2tp tunnel 9959-14 (x.x.217.67:1701): tunnel destroyed
Jun 16 08:49:22 vyos accel-l2tp: l2tp: iprange module disabled, improper IP configuration of PPP interfaces may cause kernel soft lockup
Jun 16 08:49:22 vyos ntpd[1476]: Deleting interface #7 l2tp0, 10.255.255.0#123, interface stats: received=0, sent=0, dropped=0, active_time=202 secs
Jun 16 08:49:42 vyos charon: 13[NET] received packet: from x.x.217.67[500] to y.y.96.14[500] (408 bytes)
Jun 16 08:49:42 vyos charon: 13[ENC] parsed ID_PROT request 0 [ SA V V V V V V V V ]
Jun 16 08:49:42 vyos charon: 13[ENC] received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:01
Jun 16 08:49:42 vyos charon: 13[IKE] received MS NT5 ISAKMPOAKLEY vendor ID
Jun 16 08:49:42 vyos charon: 13[IKE] received NAT-T (RFC 3947) vendor ID
Jun 16 08:49:42 vyos charon: 13[IKE] received draft-ietf-ipsec-nat-t-ike-02\n vendor ID
Jun 16 08:49:42 vyos charon: 13[IKE] received FRAGMENTATION vendor ID
Jun 16 08:49:42 vyos charon: 13[ENC] received unknown vendor ID: fb:1d:e3:cd:f3:41:b7:ea:16:b7:e5:be:08:55:f1:20
Jun 16 08:49:42 vyos charon: 13[ENC] received unknown vendor ID: 26:24:4d:38:ed:db:61:b3:17:2a:36:e3:d0:cf:b8:19
Jun 16 08:49:42 vyos charon: 13[ENC] received unknown vendor ID: e3:a5:96:6a:76:37:9f:e7:07:22:82:31:e5:ce:86:52
Jun 16 08:49:42 vyos charon: 13[IKE] x.x.217.67 is initiating a Main Mode IKE_SA
Jun 16 08:49:42 vyos charon: 13[CFG] selected proposal: IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024
Jun 16 08:49:42 vyos charon: 13[ENC] generating ID_PROT response 0 [ SA V V V V ]
Jun 16 08:49:42 vyos charon: 13[NET] sending packet: from y.y.96.14[500] to x.x.217.67[500] (156 bytes)
Jun 16 08:49:42 vyos charon: 12[NET] received packet: from x.x.217.67[500] to y.y.96.14[500] (260 bytes)
Jun 16 08:49:42 vyos charon: 12[ENC] parsed ID_PROT request 0 [ KE No NAT-D NAT-D ]
Jun 16 08:49:42 vyos charon: 12[IKE] remote host is behind NAT
Jun 16 08:49:42 vyos charon: 12[ENC] generating ID_PROT response 0 [ KE No NAT-D NAT-D ]
Jun 16 08:49:42 vyos charon: 12[NET] sending packet: from y.y.96.14[500] to x.x.217.67[500] (244 bytes)
Jun 16 08:49:42 vyos charon: 14[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (68 bytes)
Jun 16 08:49:42 vyos charon: 14[ENC] parsed ID_PROT request 0 [ ID HASH ]
Jun 16 08:49:42 vyos charon: 14[CFG] looking for pre-shared key peer configs matching y.y.96.14…x.x.217.67[192.168.2.88]
Jun 16 08:49:42 vyos charon: 14[CFG] selected peer config “remote-access”
Jun 16 08:49:42 vyos charon: 14[IKE] detected reauth of existing IKE_SA, adopting 2 children and 0 virtual IPs
Jun 16 08:49:42 vyos charon: 14[IKE] schedule delete of duplicate IKE_SA for peer ‘192.168.2.88’ due to uniqueness policy and suspected reauthentication
Jun 16 08:49:42 vyos charon: 14[IKE] IKE_SA remote-access[8] established between y.y.96.14[y.y.96.14]…x.x.217.67[192.168.2.88]
Jun 16 08:49:42 vyos charon: 14[IKE] DPD not supported by peer, disabled
Jun 16 08:49:42 vyos charon: 14[ENC] generating ID_PROT response 0 [ ID HASH ]
Jun 16 08:49:42 vyos charon: 14[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (68 bytes)
Jun 16 08:49:42 vyos charon: 16[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (436 bytes)
Jun 16 08:49:42 vyos charon: 16[ENC] parsed QUICK_MODE request 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
Jun 16 08:49:42 vyos charon: 16[CFG] selected proposal: ESP:AES_CBC_256/HMAC_SHA1_96/NO_EXT_SEQ
Jun 16 08:49:42 vyos charon: 16[IKE] received 3600s lifetime, configured 0s
Jun 16 08:49:42 vyos charon: 16[IKE] received 250000000 lifebytes, configured 0
Jun 16 08:49:42 vyos charon: 16[IKE] detected rekeying of CHILD_SA remote-access{7}
Jun 16 08:49:42 vyos charon: 16[ENC] generating QUICK_MODE response 1 [ HASH SA No ID ID NAT-OA NAT-OA ]
Jun 16 08:49:42 vyos charon: 16[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (204 bytes)
Jun 16 08:49:42 vyos charon: 06[NET] received packet: from x.x.217.67[4500] to y.y.96.14[4500] (60 bytes)
Jun 16 08:49:42 vyos charon: 06[ENC] parsed QUICK_MODE request 1 [ HASH ]
Jun 16 08:49:42 vyos charon: 06[IKE] CHILD_SA remote-access{8} established with SPIs c54860f4_i 6a361b8c_o and TS y.y.96.14/32[udp/l2f] === x.x.217.67/32[udp/l2f]
Jun 16 08:49:42 vyos accel-l2tp: l2tp: recv [L2TP tid=0 sid=0 Ns=0 Nr=0 <Protocol-Version 256> <Framing-Capabilities 1> <Bearer-Capabilities 0> <Firmware-Revision 2560> <Assigned-Tunnel-ID 15> <Recv-Window-Size 8>]
Jun 16 08:49:42 vyos accel-l2tp: l2tp: handling SCCRQ from x.x.217.67
Jun 16 08:49:42 vyos accel-l2tp: l2tp: new tunnel 22439-15 created following reception of SCCRQ from x.x.217.67:1701
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): sending SCCRP
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): send [L2TP tid=15 sid=0 Ns=0 Nr=1 <Protocol-Version 256> <Framing-Capabilities 1> <Assigned-Tunnel-ID 22439> <Recv-Window-Size 16>]
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): recv [L2TP tid=22439 sid=0 Ns=1 Nr=1 ]
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): handling SCCCN
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): established at y.y.96.14:1701
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): recv [L2TP tid=22439 sid=0 Ns=2 Nr=1 <Assigned-Session-ID 1> <Call-Serial-Number 0> <Bearer-Type 2>]
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): handling ICRQ
Jun 16 08:49:42 vyos accel-l2tp: l2tp session 22439-15, 50483-1: sending ICRP
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): new session 50483-1 created following reception of ICRQ
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): send [L2TP tid=15 sid=1 Ns=1 Nr=3 <Assigned-Session-ID -15053>]
Jun 16 08:49:42 vyos accel-l2tp: l2tp tunnel 22439-15 (x.x.217.67:1701): recv [L2TP tid=22439 sid=50483 Ns=3 Nr=2 <TX-Speed 400000000> <Framing-Type 1> <Proxy-Authen-Type 4>]
Jun 16 08:49:42 vyos accel-l2tp: l2tp session 22439-15, 50483-1: handling ICCN
Jun 16 08:49:42 vyos accel-l2tp: :: starting data channel for l2tp(x.x.217.67:1701 session 22439-15, 50483-1)
Jun 16 08:49:42 vyos accel-l2tp: :: send [LCP ConfReq id=6a <mru 1436> <magic 2c1b032b>]
Jun 16 08:49:42 vyos accel-l2tp: :: recv [LCP ConfReq id=0 <mru 1400> <magic 27bc49fe> ]
Jun 16 08:49:42 vyos accel-l2tp: :: send [LCP ConfRej id=0 ]
Jun 16 08:49:42 vyos accel-l2tp: :: recv [LCP ConfReq id=1 <mru 1400> <magic 27bc49fe>]
Jun 16 08:49:42 vyos accel-l2tp: :: send [LCP ConfAck id=1 ]
Jun 16 08:49:45 vyos accel-l2tp: :: send [LCP ConfReq id=6a <mru 1436> <magic 2c1b032b>]
Jun 16 08:49:45 vyos accel-l2tp: :: recv [LCP ConfAck id=6a <mru 1436> <magic 2c1b032b>]
Jun 16 08:49:45 vyos accel-l2tp: :: send [MSCHAP-v2 Challenge id=1 ]
Jun 16 08:49:45 vyos accel-l2tp: :: recv [MSCHAP-v2 Response id=1 <16795f88c1c1a1a97930197a5082ea27>, <2b3e4815cec3d85c3dc95dc1526b454a07f5672cffeb174>, F=0, name="[email protected]"]
Jun 16 08:49:45 vyos accel-l2tp: :: send [RADIUS(1) Access-Request id=1 <User-Name “[email protected]”> <NAS-Identifier “y.y.96.14”> <Calling-Station-Id “x.x.217.67”> <Called-Station-Id “y.y.96.14”> <MS-CHAP-Challenge 0xe1d43f4ef145491dd448c2f4bf725557> <MS-CHAP2-Response 0x010016795f88c1c1a1a97930197a5082ea2700000000000000002b3e48150cec3d85c3dc95dc1526b454a07f5672cffeb174>]
Jun 16 08:49:47 vyos accel-l2tp: :: recv [MSCHAP-v2 Response id=1 <16795f88c1c1a1a97930197a5082ea27>, <2b3e4815cec3d85c3dc95dc1526b454a07f5672cffeb174>, F=0, name="[email protected]"]
Jun 16 08:49:49 vyos accel-l2tp: :: recv [RADIUS(1) Access-Accept id=1 <Class 0xac3a093b0000013700010200c10f603c000000007c3c5746a5a3743501d643b6ea8ef60e0000000000000001> <MS-MPPE-Recv-Key 0x800150d333502121727f93cafeda1d63c88dcd4fa108a2095a416d18670de95c0018> <MS-MPPE-Send-Key 0x8002e3af53f147a1aa2738c360d71a14561d708b11330b5975886496c39768bea8aa> <MS-CHAP2-Success 0x01533d30344346344335334143334644344130393735393346424434323730353246313935354544433746> <MS-CHAP-Domain “#001DOMAIN”>]
Jun 16 08:49:49 vyos accel-l2tp: :: mppe: 128-bit session keys not allowed, disabling mppe …
Jun 16 08:49:49 vyos netplugd[986]: ppp0: ignoring event
Jun 16 08:49:49 vyos netplugd[986]: ppp0: ignoring event
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: connect: ppp0 ↔ l2tp(x.x.217.67:1701 session 22439-15, 50483-1)
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [MSCHAP-v2 Success id=1 “S=04CF4C53AC3FD4A097593FBD427052F1955EDC7F M=Authentication succeeded”]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: [email protected]: authentication succeeded
Jun 16 08:49:49 vyos systemd-udevd[3168]: link_config: autonegotiation is unset or enabled, the speed and duplex are not writable.
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: IPV6CP: discarding packet
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [LCP ProtoRej id=108 <8057>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: CCP: discarding packet
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [LCP ProtoRej id=109 <80fd>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: recv [IPCP ConfReq id=4 <addr 0.0.0.0> <dns1 0.0.0.0> <wins1 0.0.0.0> <dns2 0.0.0.0> <wins2 0.0.0.0>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [IPCP ConfReq id=c5 <addr 10.255.255.0>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [IPCP ConfRej id=4 <wins1 0.0.0.0> <wins2 0.0.0.0>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: recv [IPCP ConfAck id=c5 <addr 10.255.255.0>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: recv [IPCP ConfReq id=5 <addr 0.0.0.0> <dns1 0.0.0.0> <dns2 0.0.0.0>]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [IPCP ConfNak id=5 <addr 172.22.0.0> ]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: recv [IPCP ConfReq id=6 <addr 172.22.0.0> ]
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: send [IPCP ConfAck id=6]
Jun 16 08:49:49 vyos kernel: [ 2903.400663] l2tp0: renamed from ppp0
Jun 16 08:49:49 vyos netplugd[986]: l2tp0: ignoring event
Jun 16 08:49:49 vyos accel-l2tp: ppp0:[email protected]: rename interface to ‘l2tp0’
Jun 16 08:49:49 vyos accel-l2tp: l2tp0:[email protected]: send [RADIUS(1) Accounting-Request id=1 <User-Name “[email protected]”> <NAS-Identifier “y.y.96.14”> <NAS-Port 0> <NAS-Port-Id “l2tp0”> <Calling-Station-Id “x.x.217.67”> <Called-Station-Id “y.y.96.14”> <Class 0xac3a093b0000013700010200c10f603c000000007c3c5746a5a3743501d643b6ea8ef60e0000000000000001> <Acct-Session-Id “c7e8f1f2ca680093”> <Acct-Session-Time 0> <Acct-Input-Octets 0> <Acct-Output-Octets 0> <Acct-Input-Packets 0> <Acct-Output-Packets 0> <Acct-Input-Gigawords 0> <Acct-Output-Gigawords 0> <Framed-IP-Address 172.22.0.0>]
Jun 16 08:49:52 vyos charon: 10[IKE] deleting IKE_SA remote-access[7] between y.y.96.14[y.y.96.14]…x.x.217.67[192.168.2.88]
Jun 16 08:49:52 vyos charon: 10[IKE] sending DELETE for IKE_SA remote-access[7]
Jun 16 08:49:52 vyos charon: 10[ENC] generating INFORMATIONAL_V1 request 2022811798 [ HASH D ]
Jun 16 08:49:52 vyos charon: 10[NET] sending packet: from y.y.96.14[4500] to x.x.217.67[4500] (84 bytes)
Jun 16 08:54:49 vyos accel-l2tp: l2tp0:[email protected]: send [RADIUS(1) Accounting-Request id=1 <User-Name “[email protected]”> <NAS-Identifier “y.y.96.14”> <NAS-Port 0> <NAS-Port-Id “l2tp0”> <Calling-Station-Id “x.x.217.67”> <Called-Station-Id “y.y.96.14”> <Class 0xac3a093b0000013700010200c10f603c000000007c3c5746a5a3743501d643b6ea8ef60e0000000000000001> <Acct-Session-Id “c7e8f1f2ca680093”> <Acct-Session-Time 0> <Acct-Input-Octets 0> <Acct-Output-Octets 0> <Acct-Input-Packets 0> <Acct-Output-Packets 0> <Acct-Input-Gigawords 0> <Acct-Output-Gigawords 0> <Framed-IP-Address 172.22.0.0>]