Hello!
I’m currently working on building out a lab in GNS3. for testing out some network changes I’m doing on my personal infra with a few friends. The new setup will primarily be MikroTik based (due to already having the hardware, and wanting routing running on separate hardware as it’s a colo’d server and I want remote access in case of issues on the server itself).
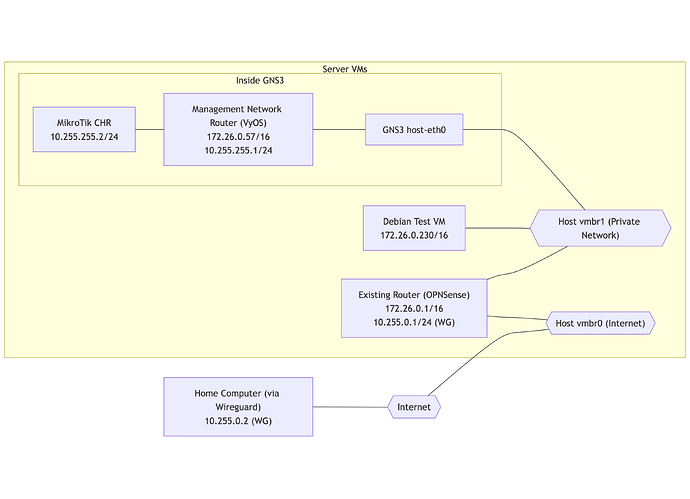
In my lab environment in GNS3, I have a MikroTik CHR with the two interfaces i’d be using on the physical device, and an additional interface going to a VyOS router for a sort of “lab management network”, which has one interface going to the CHR and one to a “physical” network (VM network on the GNS3 host machine). I’m connected to that network over Wireguard, and there’s several other VMs as well.
Here’s a simplified diagram of the network, including the host networks and how I’m connected:
The reason I’m using a lab management network and not attaching the CHR directly to the host’s vmbr1 via host-eth0 is because I’m aiming for the CHR (or rather, the hardware that will be running mostly-the-same config as the CHR) to be a drop-in replacement for OPNSense, including its networks, so it would already be aware of that subnet as it’s used elsewhere in the GNS3 project.
In VyOS, I have this configuration (simplified by removing defaults for the forum thread):
interfaces {
ethernet eth0 {
address 172.26.0.57/16
hw-id 0c:08:81:15:00:00
}
ethernet eth1 {
address 10.255.255.1/24
hw-id 0c:08:81:15:00:01
}
}
nat {
destination {
rule 1 {
description "Remap connections to routers IP to DUT IP"
destination {
address 172.26.0.57
}
inbound-interface {
name eth0
}
log
translation {
address 10.255.255.2
}
}
}
source {
rule 1 {
description "On connections to DUT, use routers internal IP"
outbound-interface {
name eth1
}
source {
address 0.0.0.0/0
}
translation {
address masquerade
}
}
}
}
protocols {
static {
route 10.255.0.0/24 {
description "Route to WireGuard via existing prod router"
next-hop 172.26.0.1 {
}
}
}
}
With this configuration, I am able to ping 172.26.0.57 and see the ping (via wireshark) end up at 10.255.255.2 (the CHR) from any machines on my network, either directly on the server or via WireGuard.
This is where it gets weird, though: From OPNSense itself and from my home machine over WireGuard, I can do curl http://172.26.0.57 and get something back from the CHR. On any other machines - such as a Debian test VM on the server - the connection times out.
Looking in Wireshark, the connections that succeed do (obviously) have traffic shown going from the VyOS instance to the CHR. On the connections that fail, it looks like VyOS didn’t even try to do anything - there’s no traffic generated on the link between VyOS eth1 and the CHR, and it seems VyOS just ignores the connection entirely on eth0. From what I can tell, this would not be caused by firewall rules, either, as the defaults seem to be to just allow all traffic - and this is the behavior I’ve seen on other parts of my lab network (not pictured, but effectively a simplified internet connection for validating firewall rules on the CHR and making sure I’m configuring it correctly).
Does anyone have any ideas what would cause this and how I would fix it?
edit: Also, if needed, I can attach packet captures of each side of VyOS - one on the link between the host and VyOS eth0 and one on the link between VyOS eth1 and the CHR/