Hi
After VyOS Team helps me with this topic " PKI and IPSec IKEv2 site-to-site VPN ", I did " PKI and IPSec IKEv2 Remote-Access VPN " between two VyOS.
I wanted to share it here so that it is available to everyone.
I considered one VyOS as a CA and one as a Client. After generating a certificate for VyOS-CA and VyOS-Client, I use Strongswan for config CA and Client.
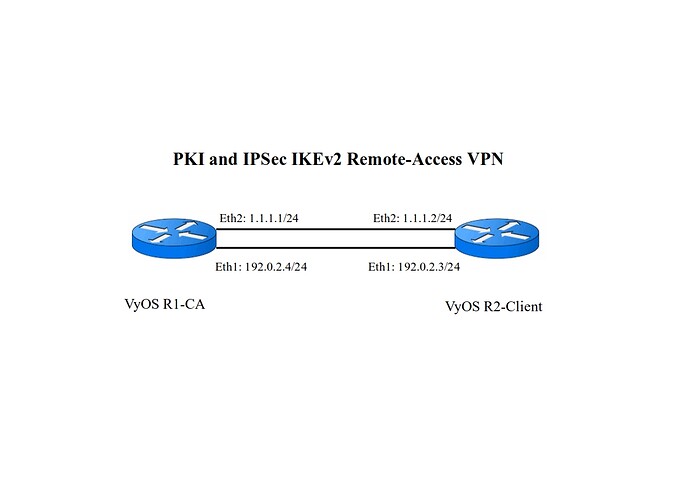
Topology:
VyOS R1-CA:
connections {
ra-rw {
remote_addrs = %any
local_addrs = 192.0.2.4
proposals = aes128gcm128-sha256-modp2048
version = 2
send_certreq = no
rekey_time = 7200s
keyingtries = 1
pools = ra-rw-ipv4
local {
id = "C=GB, ST=Some-State, L=Some-City, O=VyOS, CN=R1"
auth = pubkey
certs = R1.pem
}
remote {
auth = eap-mschapv2
id = "C=GB, ST=Some-State, L=Some-City, O=VyOS, CN=R2"
eap_id = %any
}
children {
ikev2-vpn {
esp_proposals = aes128gcm128-sha256
rekey_time = 3600s
rand_time = 540s
dpd_action = clear
inactivity = 28800
local_ts = 1.1.1.0/24
remote_ts = 1.1.1.0/24
}
}
}
}
pools {
ra-rw-ipv4 {
addrs = 192.0.2.3/24
dns = 192.0.2.4
}
}
secrets {
eap-vyos {
secret = "vyos"
id = "vyos"
}
}
ipsec.secrets for VyOS-CA:
: RSA “/etc/swanctl/private/x509_R1.pem”
vyos : EAP “vyos”
VyOS R2-Client:
connections {
ra-rw {
remote_addrs = 192.0.2.4
local_addrs = 192.0.2.3
proposals = aes128gcm128-sha256-modp2048
version = 2
local {
id = "C=GB, ST=Some-State, L=Some-City, O=VyOS, CN=R2"
eap_id = vyos
auth = eap
}
remote {
auth = pubkey
id = "C=GB, ST=Some-State, L=Some-City, O=VyOS, CN=R1"
}
children {
ikev2-vpn {
esp_proposals = aes128gcm128-sha256
local_ts = 1.1.1.0/24
remote_ts = 1.1.1.0/24
}
}
}
}
secrets {
eap-vyos {
secret = "vyos"
id = "vyos"
}
}
ipsec.secrets for VyOS-Client:
vyos : EAP “vyos”
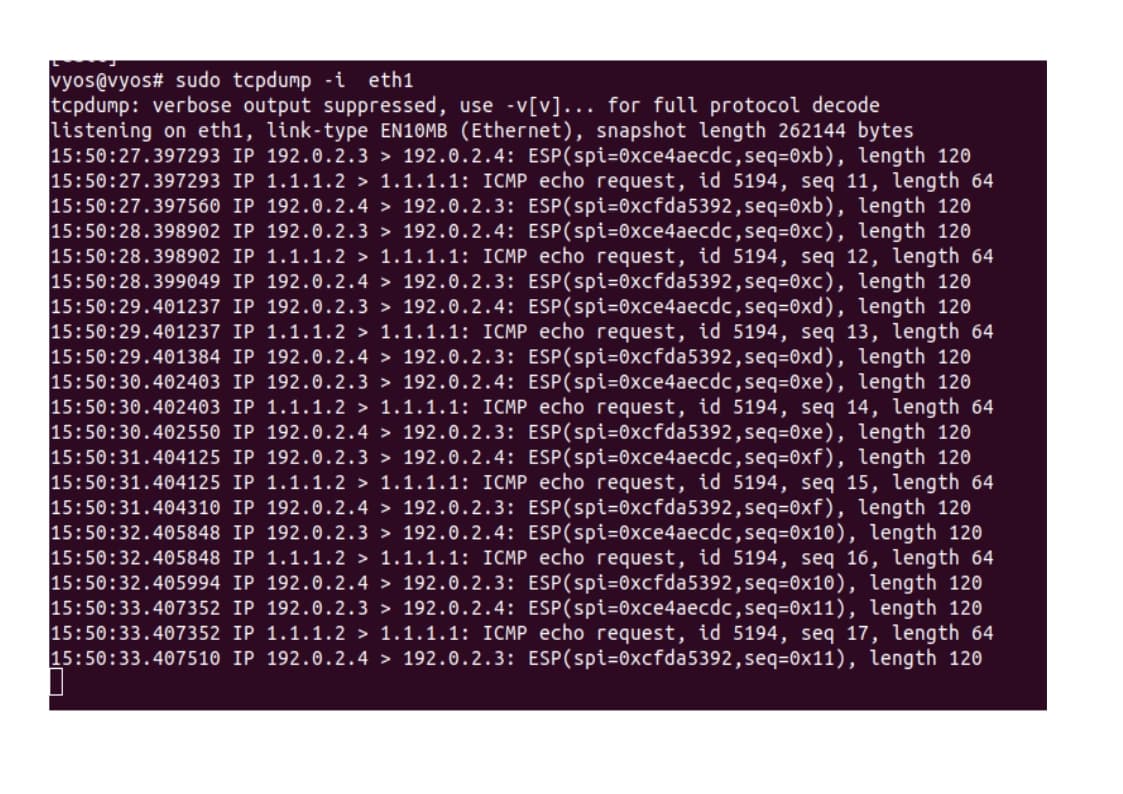
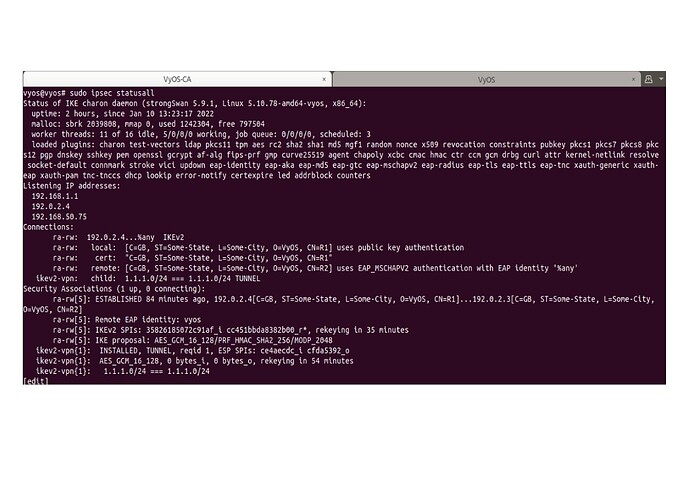
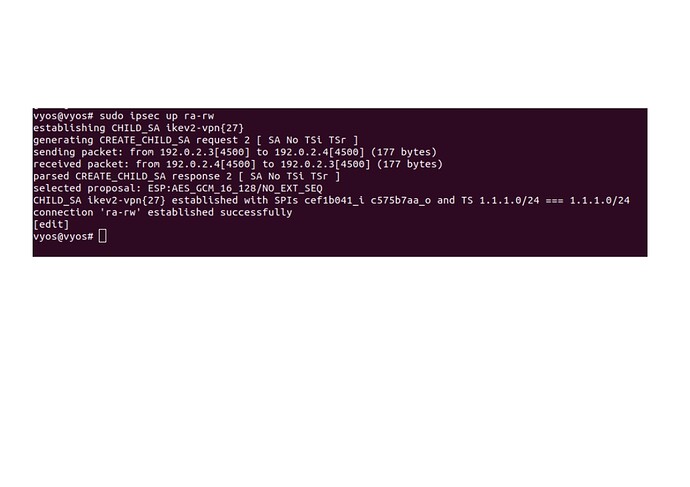
Results:
tcpdump:
ipsec statusall:
ipsec up ra-rw:
daemon: (sudo journalctl -b /usr/lib/ipsec/charon | tee):
Thanks to the VyOS team for their help.