hello VyOS Team,
How can I simulate this scenario “PKI and IPSec IKEv2 site-to-site VPN” in VyOS?
Add cert and use it instead of psk
I considered one VyOS as a CA and one as a Client.
I used these Configuration “⚓ T3985 vpn IPSec site-to-site continues to work if certificates are deleted” on the CA side. of course, I used IKEv2. but I don’t know what Configuration to use on the Client side for authentication??
Try the settings from here (x.509 certificates):
It’s great, Thank you for your help, Nikolay. 
Thank you too for tell to me the Client-side configurations in the following scenario:
“PKI and IPSec IKEv2 remote-access VPN”.
hi
if you need to create a road-warrior vpn with ipsec Ikev2 , here is an example with the common settings with PKI and some clients configurations:
Yes, I saw this link " PKI and IPSec IKEv2 remote-access VPN " and This link does not say anything about client configuration.
I Configured VyOS as a remote CA, But I can’t Configure the Client-side.
Thank you for your help. ![]()
please check it! there are two examples with Windows 10/IOS (apple)
Client Configuration
Configuring VyOS to act as your IPSec access concentrator is one thing, but you also need to setup your client connecting to the server so they can talk to the IPSec gateway.
Microsoft Windows (10+)
Can I use Ubuntu or VyOS on the client side?
Yes , you can use Ubuntu .it’s possible that you need installs strongswan plugin(in your lapto/desktop ) and share the CA . link below there is some example:
Thanks for your help, Fernando.
I use Strongswan for the client-side and set the following config but I still could not do this scenario.
SCENARIO: Example PKI and IPSec IKEv2 Remote VPN:
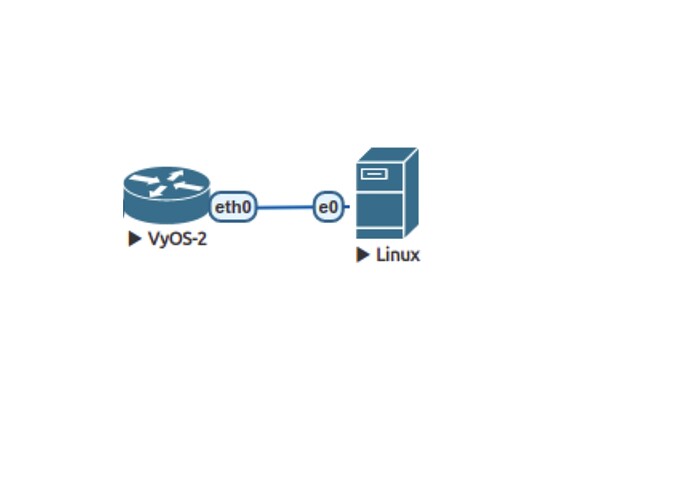
Topology:
VyOS Config:
IPsec between VyOS and Ubuntu with VyOS as a CA for x509 certs
VyOS chosen as CA
vyos@vyos:~$ generate pki ca install CA
set pki ca CA certificate ‘MIIDnTCCAo…=’
set pki ca CA private key ‘MIIEvwIBAD…=’
ON VyOS (CA) IN NON CONFIG MODE
vyos@vyos:~$ generate pki certificate sign CA install R1
set pki certificate R1 certificate ‘MIIDrDCCA …=’
set pki certificate R1 private key ‘MIIEvgIBA…O’
on VyOS (CA cert already there. Needs: R1 cert, R1 private key):
set pki certificate R1 certificate ‘MIIDrDCCA …=’
set pki certificate R1 private key ‘MIIEvgIBA…O’
on Ubuntu (Needs: CA cert, R2 cert, R2 private key):
This Certificate was Generated for Ubuntu, and the certificate and private key should copy to this path: /etc/ipsec.d/
vyos@vyos:~$ generate pki certificate sign CA install R2
configuring our IPSec/IKE proposals
set vpn ipsec esp-group ESP-RW compression ‘disable’
set vpn ipsec esp-group ESP-RW lifetime ‘3600’
set vpn ipsec esp-group ESP-RW pfs ‘disable’
set vpn ipsec esp-group ESP-RW proposal 10 encryption ‘aes128gcm128’
set vpn ipsec esp-group ESP-RW proposal 10 hash ‘sha256’
set vpn ipsec ike-group IKE-RW key-exchange ‘ikev2’
set vpn ipsec ike-group IKE-RW lifetime ‘7200’
set vpn ipsec ike-group IKE-RW mobike ‘enable’
set vpn ipsec ike-group IKE-RW proposal 10 dh-group ‘14’
set vpn ipsec ike-group IKE-RW proposal 10 encryption ‘aes128gcm128’
set vpn ipsec ike-group IKE-RW proposal 10 hash ‘sha256’
set vpn ipsec remote-access pool ra-rw-ipv4 name-server ‘192.0.2.1’
set vpn ipsec remote-access pool ra-rw-ipv4 prefix ‘192.0.2.128/25’
set vpn ipsec remote-access connection rw authentication id ‘192.0.2.1’
set vpn ipsec remote-access connection rw authentication server-mode ‘x509’
set vpn ipsec remote-access connection rw authentication x509 ca-certificate ‘CA’
set vpn ipsec remote-access connection rw authentication x509 certificate ‘R1’
set vpn ipsec remote-access connection rw esp-group ‘ESP-RW’
set vpn ipsec remote-access connection rw ike-group ‘IKE-RW’
set vpn ipsec remote-access connection rw local-address ‘192.0.2.1’
set vpn ipsec remote-access connection rw pool ‘ra-rw-ipv4’
set vpn ipsec remote-access connection rw pool ‘ra-rw-ipv6’
set vpn ipsec remote-access connection rw authentication client-mode ‘eap-mschapv2’
set vpn ipsec remote-access connection rw authentication local-users username vyos password ‘vyos’
Client (Ubuntu) Config:
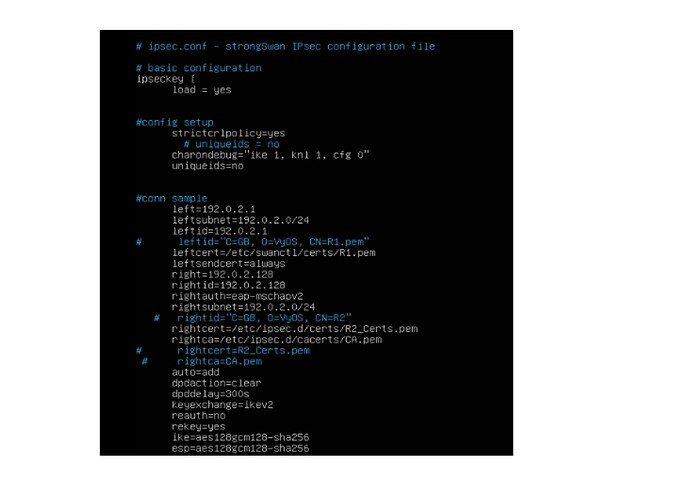
For Client-side I use Strongswan and the following configuration:
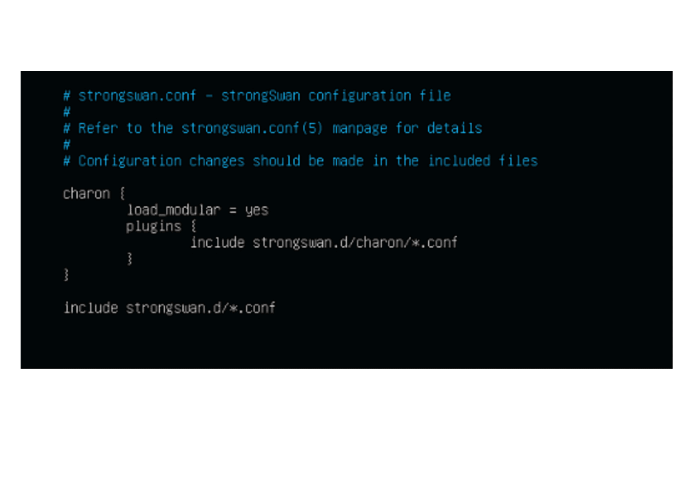
/etc/strongswan.d/charon/ipsec.conf
and /etc/strongswan.conf:
I see ICMP Packet in Ping. I can’t have ping IPSec Between VyOS and Ubuntu.
thank you very much in advance. I would appreciate any help.
Hi @Mohammad-Rastgar ,
Check the “authentication id” in the issued certificate carefully.
(In the example you can see how it might look like)
Also, looking at the logs may give a hint as to the cause of the errors:
sudo journalctl -b /usr/lib/ipsec/charon | tee
sudo journalctl -b | tee
As you said, I changed the “authentication id” like below.
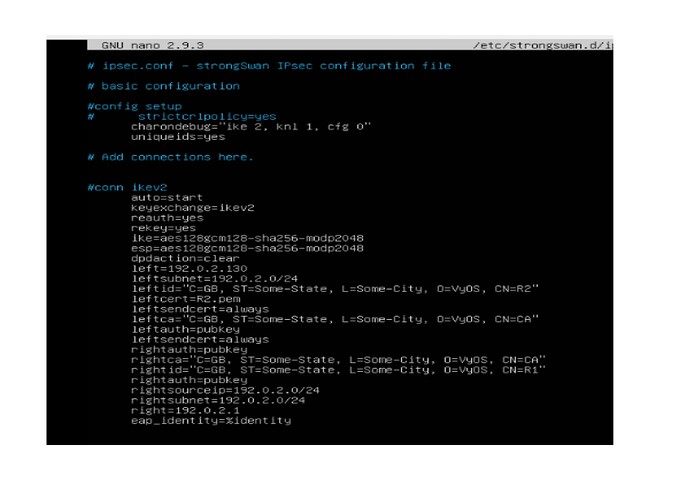
And I used the following strongswan configuration for the client-side.
path: /etc/strongswan.d/ipsec.conf
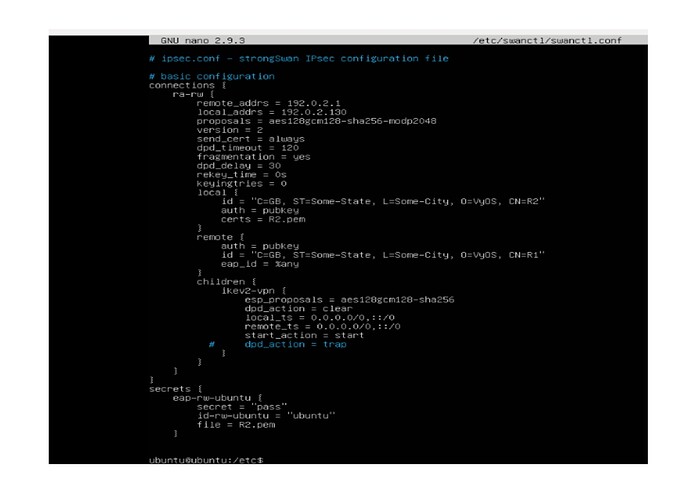
I also used the following configuration in swanctl, but the result was the same.
path: /etc/swanctl/swanctl.conf
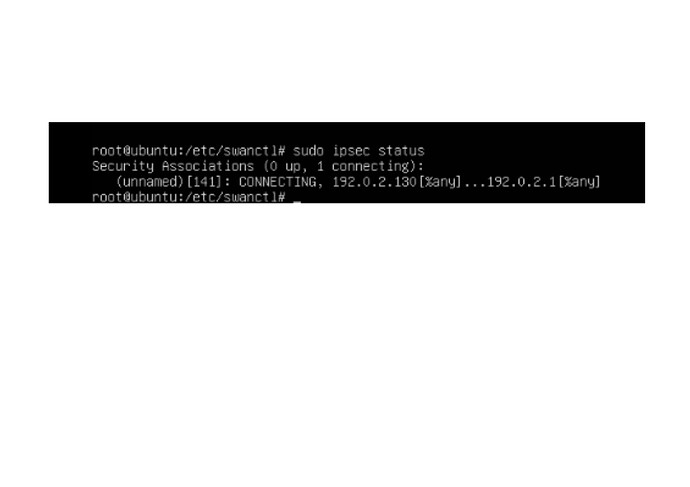
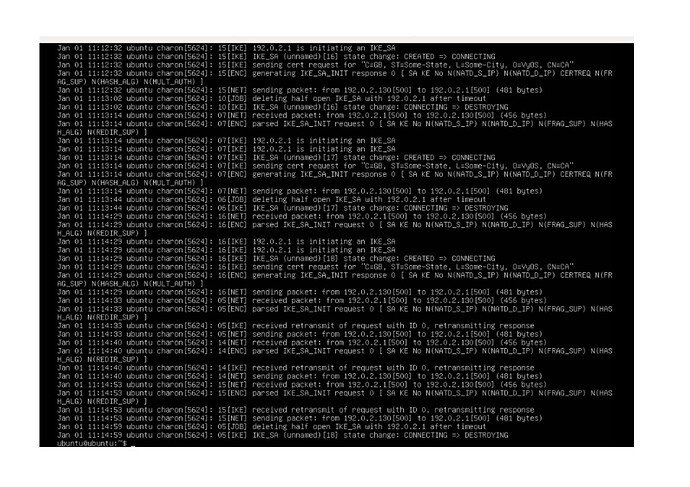
And I got the following output, but I still do not have an up IPSec connection.
This is ipsec status:
This is journalctl output:
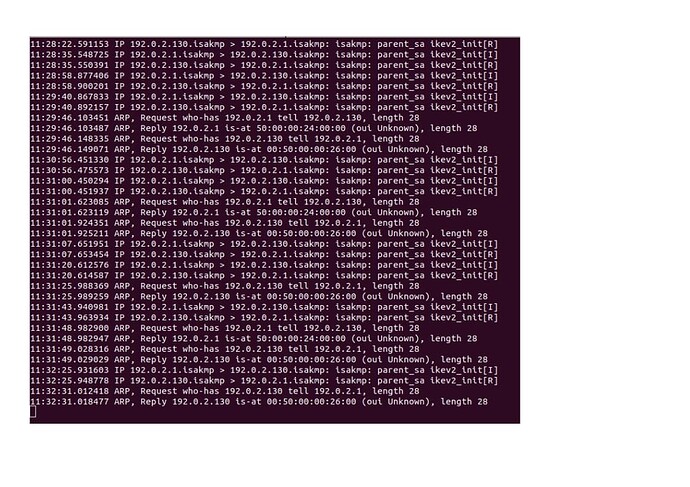
This is tcpdump in CA (VyOS):
Can you tell us what the problem is? I want to implement the PKI and IPSec IKEv2 remote access VPN scenario.
Thank you in advance for your help.