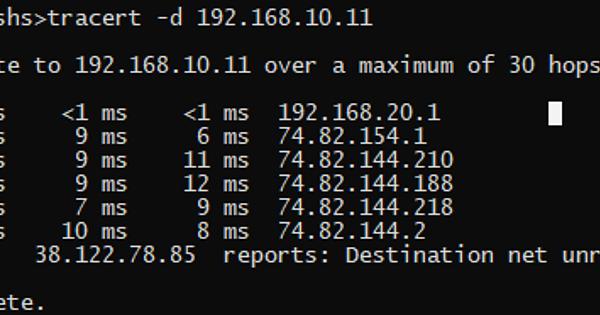
I have an original post listed here and was given a solution: “you must setup a routing policy to be ensure that all traffic for same connection will be forwarded through one external interface”. I tried setting this up and was not successful. Should I be using route-interface or just plain route? For start, I would only like VLAN 7 to run traffic through eth3 and everything else route through eth0. I initially added
set protocols static interface-route 192.168.7.0/24 eth3
set protocols static interface-route 192.168.10.0/24 eth0
set protocols static interface-route 192.168.20.0/24 eth0
set protocols static interface-route 192.168.30.0/24 eth0
set protocols static interface-route 192.168.40.0/24 eth0
set protocols static interface-route 192.168.50.0/24 eth0
set protocols static interface-route 192.168.60.0/24 eth0
set protocols static interface-route 192.168.70.0/24 eth0
set protocols static interface-route 192.168.80.0/24 eth0
set protocols static interface-route 192.168.110.0/24 eth0
and it still gave issues while both eth0 and eth3 (the WAN’s) were connected. Thanks for any help or information.