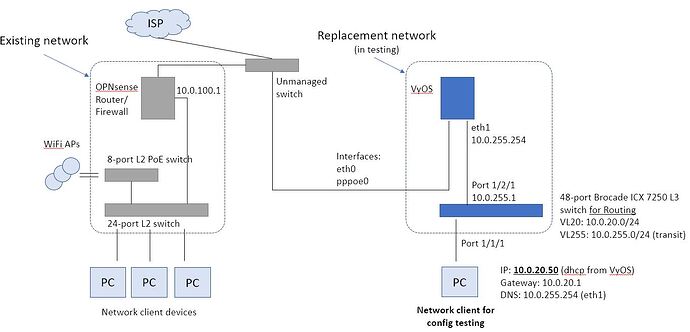
I’m configuring VyOS as a firewall to replace an alternate firewall/switching equipment I’m currently using.
The the VyOS machine and client computer (a macmini) is configured as per the image below:
I previously had a fully working configuration with VyOS plugged into my existing network via the 24-port switch. I’ve now connected it directly to internet and it is partially working for DNS resolution.
I can connect to some sites such as google.com or vyos.io and the page loads are instantaneous. But for other sites such as “forum.vyos.io” the browser just waits to load the page indefinitely and eventually fails.
I’ve tried simplifying my configuration, looking at log files and at help online but haven’t found any smoking gun to point out what is wrong so wondering if the community might have insight.
A summary of what has been changed or tried to fix the above:
- Added pppoe authentication info to configuration.
- Configured DNS forwarding, initially through a container running Adguardhome and had the same issue as above. Thought there might be an issue with container networking so I simplified to DNS forwarding through PowerDNS and removing the container altogether.
- Added firewall rules per the blog post on blog.kroy.io. Note: I’ve already tried disabling the firewall and running “naked” and it didn’t fix the problem with DNS above. I don’t believe the issue to be firewall related.
- I only have pdns listening on port 53 for tcp/udp
Netstat output:
xxxxxxx@vyos:~$ sudo netstat -ntulp | grep 53
tcp 0 0 10.0.255.254:53 0.0.0.0:* LISTEN 2479/pdns_recursor
tcp 0 0 127.0.0.1:2612 0.0.0.0:* LISTEN 1533/ldpd
udp 0 0 10.0.255.254:53 0.0.0.0:* 2479/pdns_recursor
xxxxxxx@vyos:~$
Traceroute output from macmini (it never completes)
xxxxxxx@Macmini ~ % traceroute forum.vyos.io
traceroute: Warning: forum.vyos.io has multiple addresses; using 34.233.30.99
traceroute to vyos-forum-1044462705.us-east-1.elb.amazonaws.com (34.233.30.99), 64 hops max, 52 byte packets
1 10.0.20.1 (10.0.20.1) 2.653 ms 1.087 ms 1.027 ms
2 10.0.255.254 (10.0.255.254) 0.624 ms 0.388 ms 0.396 ms
3 xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx) 2.034 ms 2.568 ms 2.978 ms
4 * * *
5 * * *
6 xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx) 4.952 ms 4.379 ms 4.175 ms
7 xxx.xxx.xxx.xxx (xxx.xxx.xxx.xxx) 3.928 ms 3.033 ms 2.980 ms
8 * * *
9 * * *
10 52.94.82.1 (52.94.82.1) 2.573 ms
52.94.81.237 (52.94.81.237) 12.146 ms
52.94.81.235 (52.94.81.235) 2.517 ms
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
continues with * * *
VyOS config:
xxxxxx@vyos:~$ show conf
firewall {
ipv4 {
name LAN-LOCAL {
default-action accept
description "Allow access from LAN to firewall"
}
name LAN-WAN {
default-action accept
description "Allow access from LAN to WAN"
}
name LOCAL-LAN {
default-action accept
description "Allow access from firewall to LAN"
}
name LOCAL-WAN {
default-action accept
description "Allow access from firewall to WAN"
}
name WAN-LAN {
default-action drop
rule 1 {
action accept
description "Allow EST/Related Traffic"
state established
state related
}
rule 100 {
action accept
description "Allow ICMP from WAN to LAN"
protocol icmp
state new
}
}
name WAN-LOCAL {
default-action drop
rule 1 {
action accept
description "Allow EST/Related Traffic"
state established
state related
}
rule 100 {
action accept
description "Allow ICMP from WAN to firewall"
protocol icmp
state new
}
}
}
zone LAN {
default-action drop
from LOCAL {
firewall {
name LOCAL-LAN
}
}
from WAN {
firewall {
name WAN-LAN
}
}
interface eth1
}
zone LOCAL {
default-action drop
from LAN {
firewall {
name LAN-LOCAL
}
}
from WAN {
firewall {
name WAN-LOCAL
}
}
local-zone
}
zone WAN {
default-action drop
from LAN {
firewall {
name LAN-WAN
}
}
from LOCAL {
firewall {
name LOCAL-WAN
}
}
interface pppoe0
}
}
interfaces {
ethernet eth0 {
description WAN
hw-id xx:xx:xx:xx:xx:xx
}
ethernet eth1 {
address 10.0.255.254/24
description LAN
hw-id xx:xx:xx:xx:xx:xx
}
ethernet eth2 {
hw-id xx:xx:xx:xx:xx:xx
}
loopback lo {
}
pppoe pppoe0 {
authentication {
password ****************
username ****************
}
description xxxxx-xxxxx
source-interface eth0
}
}
nat {
source {
rule 100 {
outbound-interface {
name pppoe0
}
source {
address 10.0.0.0/16
}
translation {
address masquerade
}
}
}
}
protocols {
static {
route 10.0.0.0/16 {
next-hop 10.0.255.1 {
}
}
}
}
service {
dhcp-server {
host-decl-name
shared-network-name LAN {
authoritative
subnet 10.0.255.0/24 {
default-router 10.0.255.1
range 0 {
start 10.0.255.50
stop 10.0.255.250
}
}
}
shared-network-name vl10_mgmt {
authoritative
domain-name home.arpa
subnet 10.0.10.0/24 {
default-router 10.0.10.1
range 0 {
start 10.0.10.50
stop 10.0.10.250
}
}
}
shared-network-name vl20_main {
authoritative
subnet 10.0.20.0/24 {
default-router 10.0.20.1
name-server 10.0.255.254
range 0 {
start 10.0.20.50
stop 10.0.20.250
}
}
}
shared-network-name vl99_sec {
authoritative
domain-name home.arpa
subnet 10.0.99.0/24 {
default-router 10.0.99.1
range 0 {
start 10.0.99.50
stop 10.0.99.250
}
}
}
}
dns {
forwarding {
allow-from 10.0.0.0/16
listen-address 10.0.255.254
name-server 9.9.9.9 {
}
name-server 149.112.112.112 {
}
}
}
ntp {
allow-client {
address 0.0.0.0/0
address ::/0
}
server 0.pool.ntp.org {
}
server 1.pool.ntp.org {
}
server 2.pool.ntp.org {
}
}
ssh {
listen-address 10.0.255.254
port 22
}
}
system {
config-management {
commit-revisions 100
}
conntrack {
modules {
ftp
h323
nfs
pptp
sip
sqlnet
tftp
}
}
console {
device ttyS0 {
speed 115200
}
}
host-name xxxxxxxx
login {
user xxxxxxxx {
authentication {
encrypted-password ****************
}
}
}
name-server 10.0.255.254
syslog {
global {
facility all {
level info
}
facility local7 {
level debug
}
}
}
time-zone US/Eastern
}
}